= Setting up certificates for verification of digital signature platform keys
Unresolved include directive in modules/admin/pages/registry-management/system-keys/control-plane-platform-certificates.adoc - include::platform:ROOT:partial$admonitions/language-ua.adoc[]
General overview
Certificates for verifying digital signature keys are used to confirm the authenticity of the public key used in the digital signing process. They are issued by a trusted organization, known as the Accredited Key Certification Center (AKCC), and they play an important role in generating trust in electronic documents and transactions.
System signature keys are designed for data signing and verification by systems or programs. In other words, they help ensure that the corresponding data package or software originates from a known source and has not been altered.
QES (Qualified electronic signature) — is an enhanced version of DES (Digital Electronic Signature). It provides a higher level of security and trust, as more reliable cryptographic algorithms and procedures are used for its creation. QES often has legal force and allows confirming the authenticity of electronic documents in legal situations."
- CACertificates.p7b та CA.json:
-
-
CACertificates.p7b: this file contains one or more certificates in
PKCS#7format. The `PKCS#7`format is widely used for exchanging and storing certificates or an entire chain of certificates." -
CA.json: this is a JSON format file that can contain details about certificates. The JSON format presents certificate information in a format that is easy to read by both humans and machines."
The platform provides extensive capabilities for certificate management: it ensures their secure upload, storage, usage, and update.
-
Adding certificates
| The AKCC certificates for verifying the system signature keys, added in the Signature Verification Data section, will be applied to the Platform settings. |
To add AKCC certificates, follow these steps:
-
Log in to the registry management administrative panel Control Plane using the previously received login and password.
-
Open menu Platform management
-
Click the
Editbutton located in the upper right corner.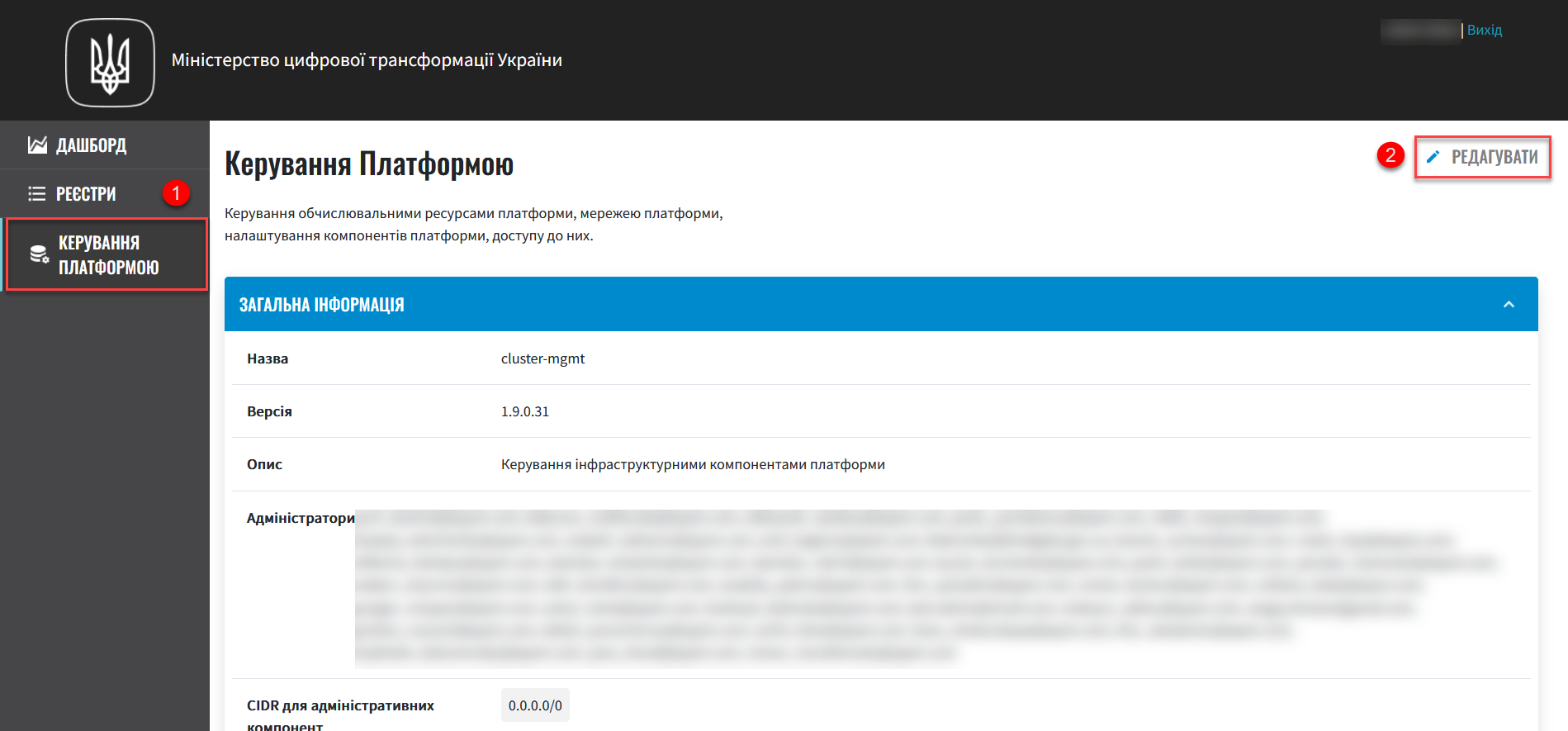
-
Go to the Signature Verification Data section.

-
Add the public AKCC certificates (CACertificates.p7b).
-
Add the list of compatible certificates (.p7b).
-
Add the certificate file by clicking the button Choose file at the Public AKCC certificates (.p7b extension). In the new window, navigate to the folder where the certificate file is stored, select it and press kbd:[Open].

-
-
Add the AKCC list (CA.json).
-
Add interaction parameters with compatible Key Certification Center (.json).
-
Add the certificate file by clicking the button Choose file at the List of AKCC (.json extension). In the new window, navigate to the folder where the certificate file is stored, select it and press kbd:[Open].

-
-
At the end, check the information entered and press the button
ConfirmAs a result of updating the key information on the Control Plane interface, a new request to update the registry configuration is created, which needs to be confirmed.
-
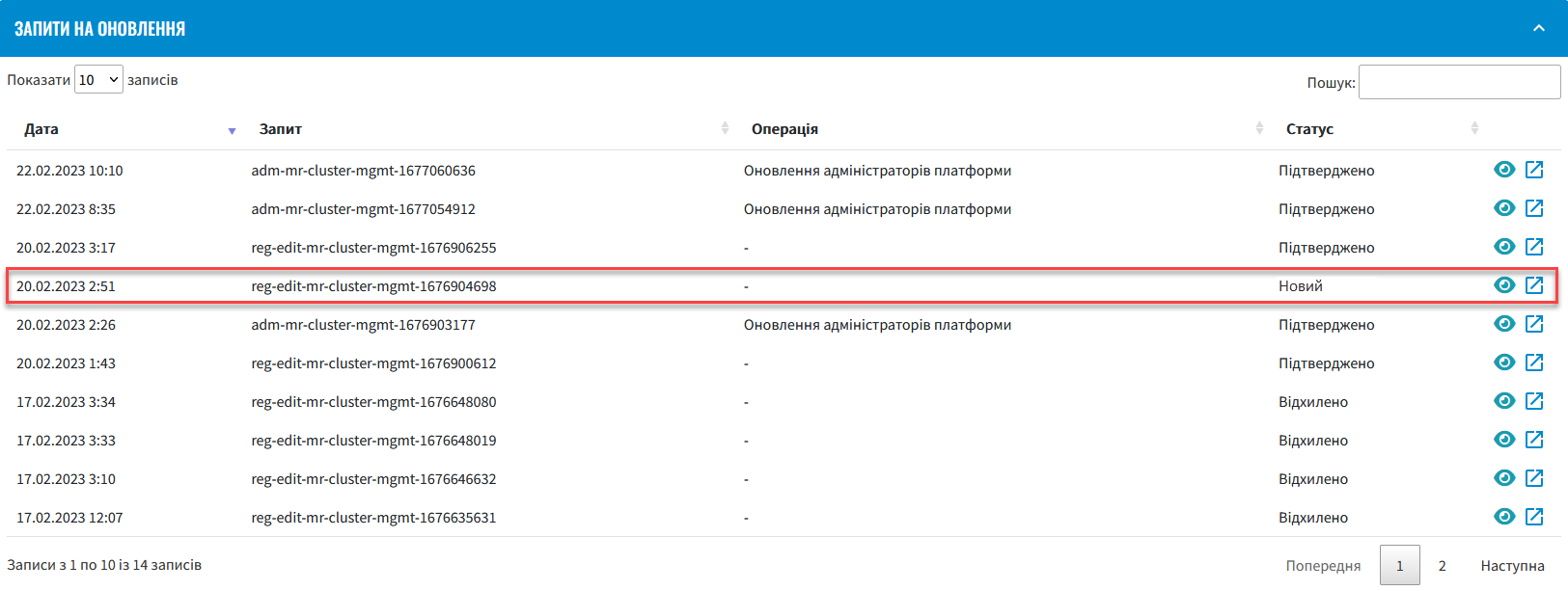
In the Control Plane admin panel interface, go back to the Platform management section, scroll down the page and find the Update requests section.
-
Scroll down the page and click on the Confirm button.

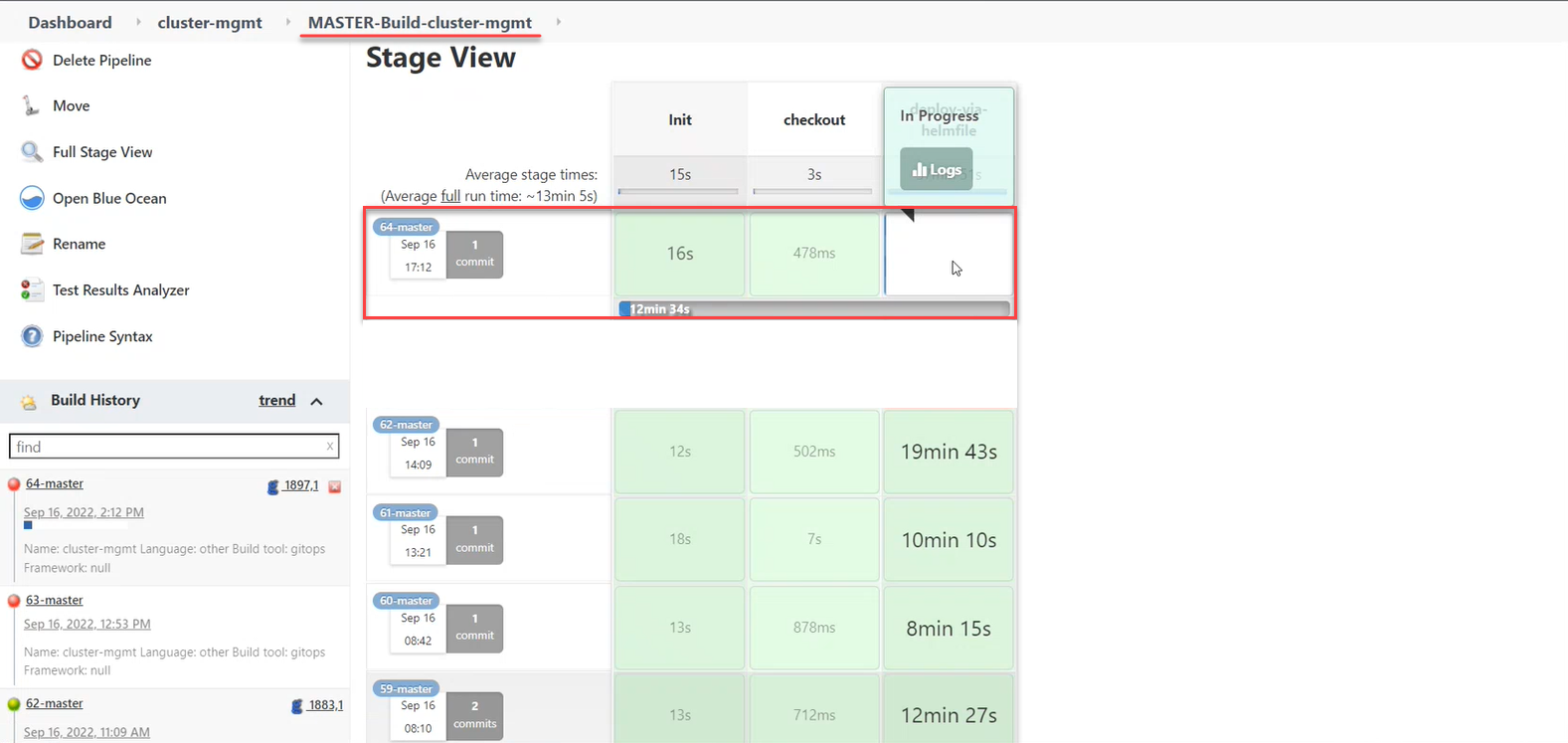
Proposed changes are made to the deploy-templates/values.yaml file configuration of the cluster-mgmtcomponent upon confirmation.Next, the
Master-Build-cluster-mgmtpipeline is automatically launched, which applies the parameters of the given configuration and creates secrets for digital signature keys. -
Wait for the code build to complete. This can take approximately 15 minutes.
You can check the current status and execution result via the
CIlink on the interface.
In the Jenkins interface, find the appropriate pipeline and track the execution status.