Secured Secrets Management for Application Deployment⚓︎
This Use Case demonstrates how to securely manage sensitive data, such as passwords, API keys, and other credentials, that are consumed by application during development or runtime in production. The approach involves storing sensitive data in an external secret store that is located in a "vault" namespace (but can be Vault, AWS Secret Store or any other provider). The process implies transmitting confidential information from the vault namespace to the deployed namespace for the purpose of establishing a connection to a database.
Roles⚓︎
This documentation is tailored for the Developers and Team Leads.
Goals⚓︎
- Make confidential information usage secure in the deployment environment.
Preconditions⚓︎
- EDP instance is configured with Gerrit, Tekton and Argo CD;
- External Secrets is installed;
- Developer has access to the EDP instances using the Single-Sign-On approach;
- Developer has the
Administratorrole (to perform merge in Gerrit); - Developer has access to manage secrets in demo-vault namespace.
Scenario⚓︎
To use External Secret in EDP approach, follow the steps below:
Add Application⚓︎
To begin, you will need an application first. Here are the steps to create it:
-
Open EDP Portal URL. Use the
Sign-Inoption: -
In the top right corner, enter the
Cluster settingsand ensure that bothDefault namespaceandAllowed namespaceare set: -
Create the new
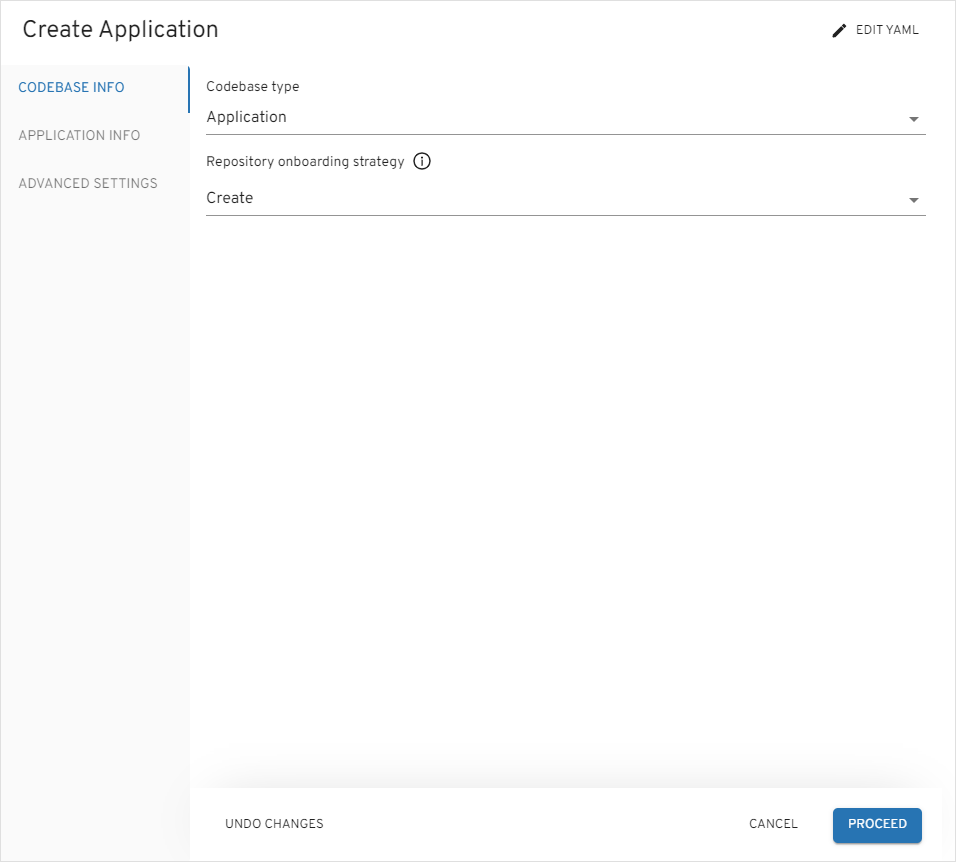
Codebasewith theApplicationtype using theCreatestrategy. To do this, click theEDPtab: -
Select the
Componentssection under the EDP tab and push the+button: -
Select the
ApplicationCodebase type because we are going to deliver our application as a container and deploy it inside the Kubernetes cluster. Select theCreatestrategy to use predefined template: -
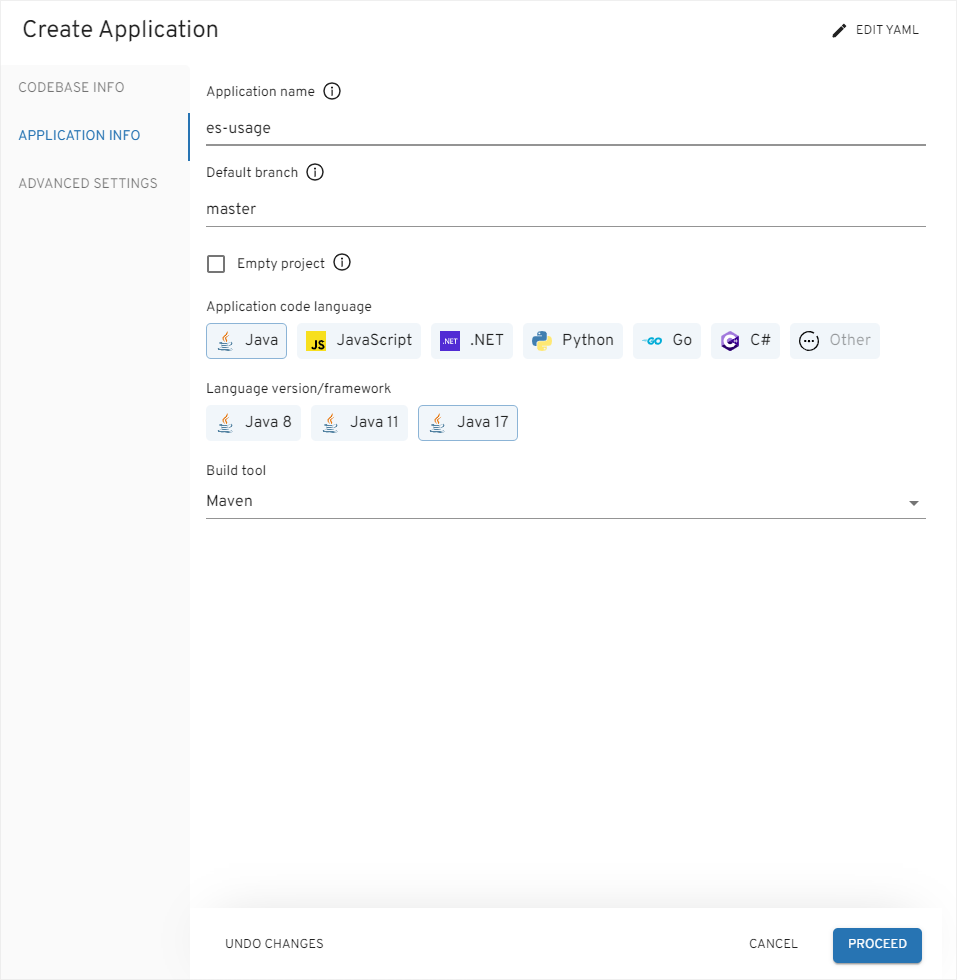
On the
Application Infotab, define the following values and press theProceedbutton:- Application name:
es-usage - Default branch:
master - Application code language:
Java - Language version/framework:
Java 17 - Build tool:
Maven
- Application name:
-
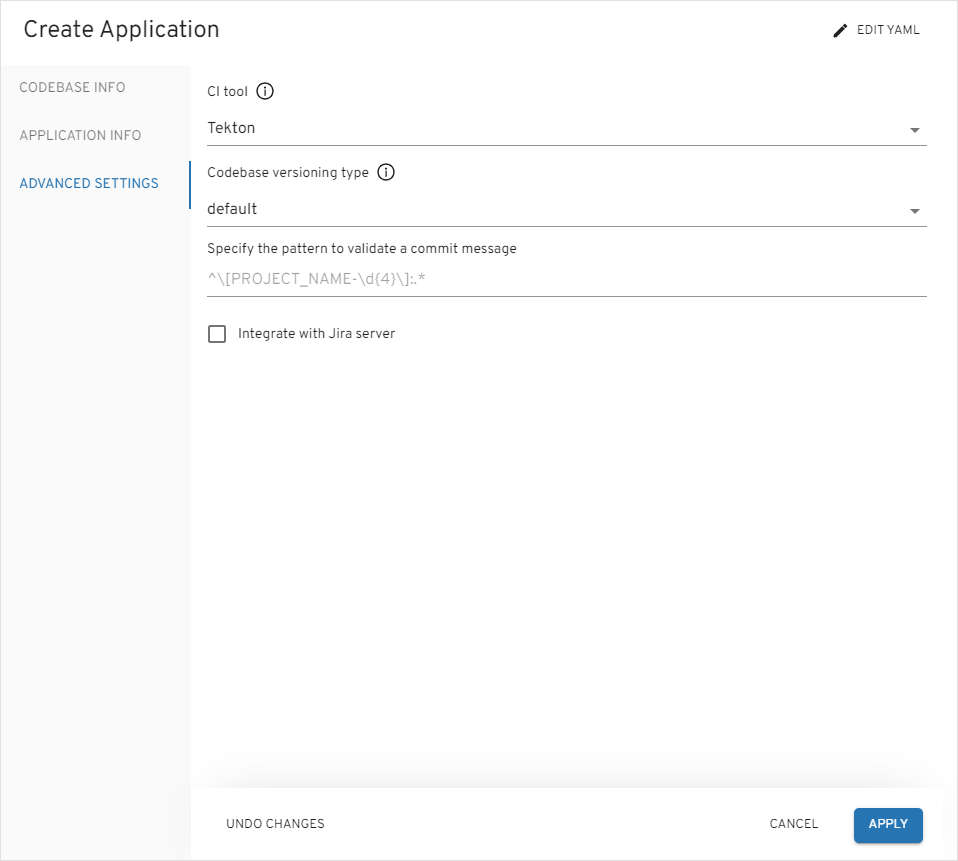
On the
Advanced Settingstab, define the below values and push theApplybutton:- CI tool:
Tekton - Codebase versioning type:
default
- CI tool:
-
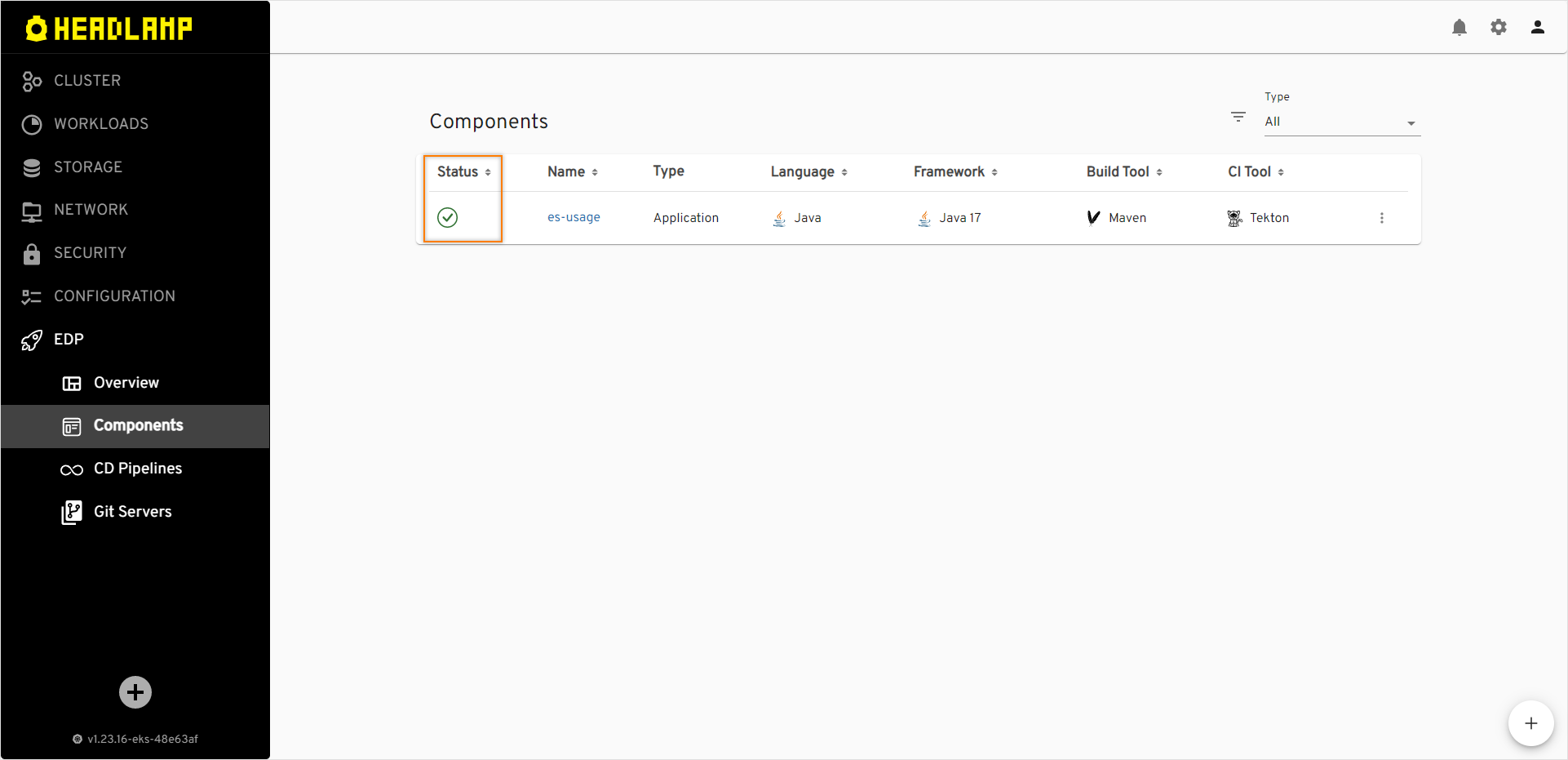
Check the application status. It should be green:
Create CD Pipeline⚓︎
This section outlines the process of establishing a CD pipeline within EDP Portal. There are two fundamental steps in this procedure:
- Build the application from the last commit of the
masterbranch;
- Create a
CD Pipelineto establish continuous delivery to the SIT environment.
To succeed with the steps above, follow the instructions below:
-
Create CD Pipeline. To enable application deployment, create a CD Pipeline with a single environment - System Integration Testing (SIT for short). Select the
CD Pipelinessection under theEDPtab and push the+button: -
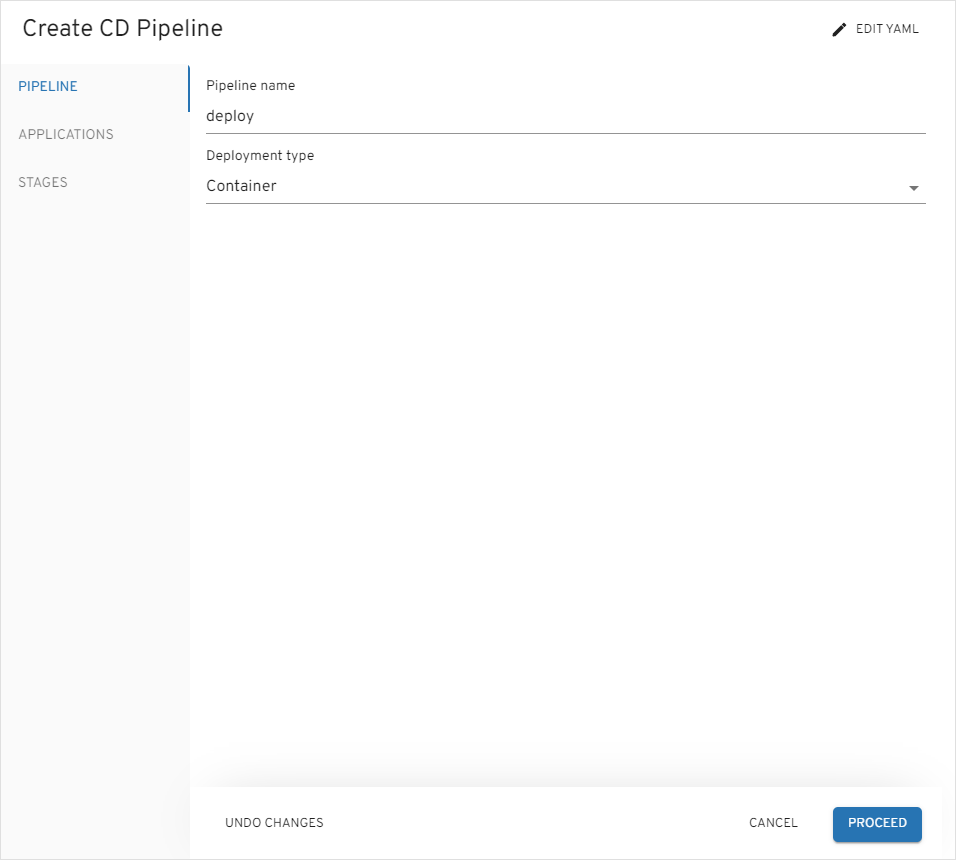
On the
Pipelinetab, define the following values and press theProceedbutton:- Pipeline name:
deploy - Deployment type:
Container
- Pipeline name:
-
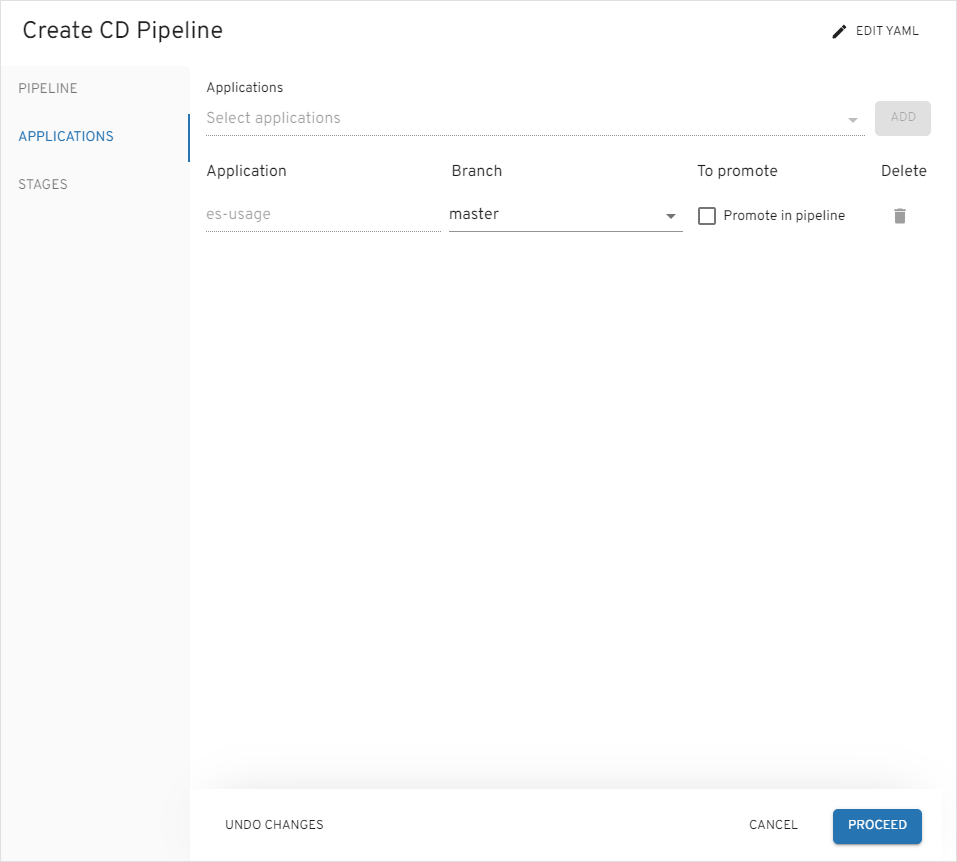
On the
Applicationstab, addes-usageapplication, selectmasterbranch, leavePromote in pipelineunchecked and press theProceedbutton: -
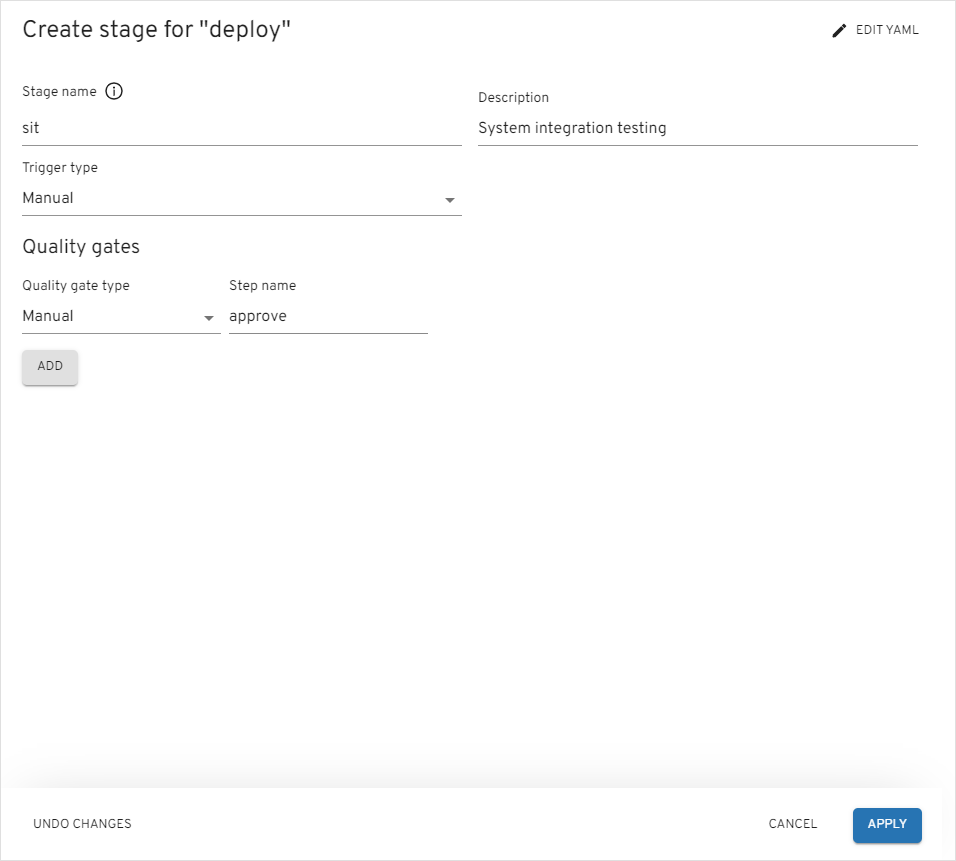
On the
Stagetab, add thesitstage with the values below and push theApplybutton:
Configure RBAC for External Secret Store⚓︎
Note
In this scenario, three namespaces are used: demo, which is the namespace where EDP is deployed, demo-vault, which is the vault where developers store secrets, anddemo-deploy-sit, which is the namespace used for deploying the application. The target namespace name for deploying application is formed with the pattern: edp-<cd_pipeline_name>-<stage_name>.
To make the system to function properly, it is imperative to create the following resources:
-
Create namespace
demo-vaultto store secrets: -
Create Secret:
-
Create Role to access the secret:
-
Create RoleBinding:
Add External Secret to Helm Chart⚓︎
Now that RBAC is configured properly, it is time to add external secrets templates to application Helm chart. Follow the instructions provided below:
-
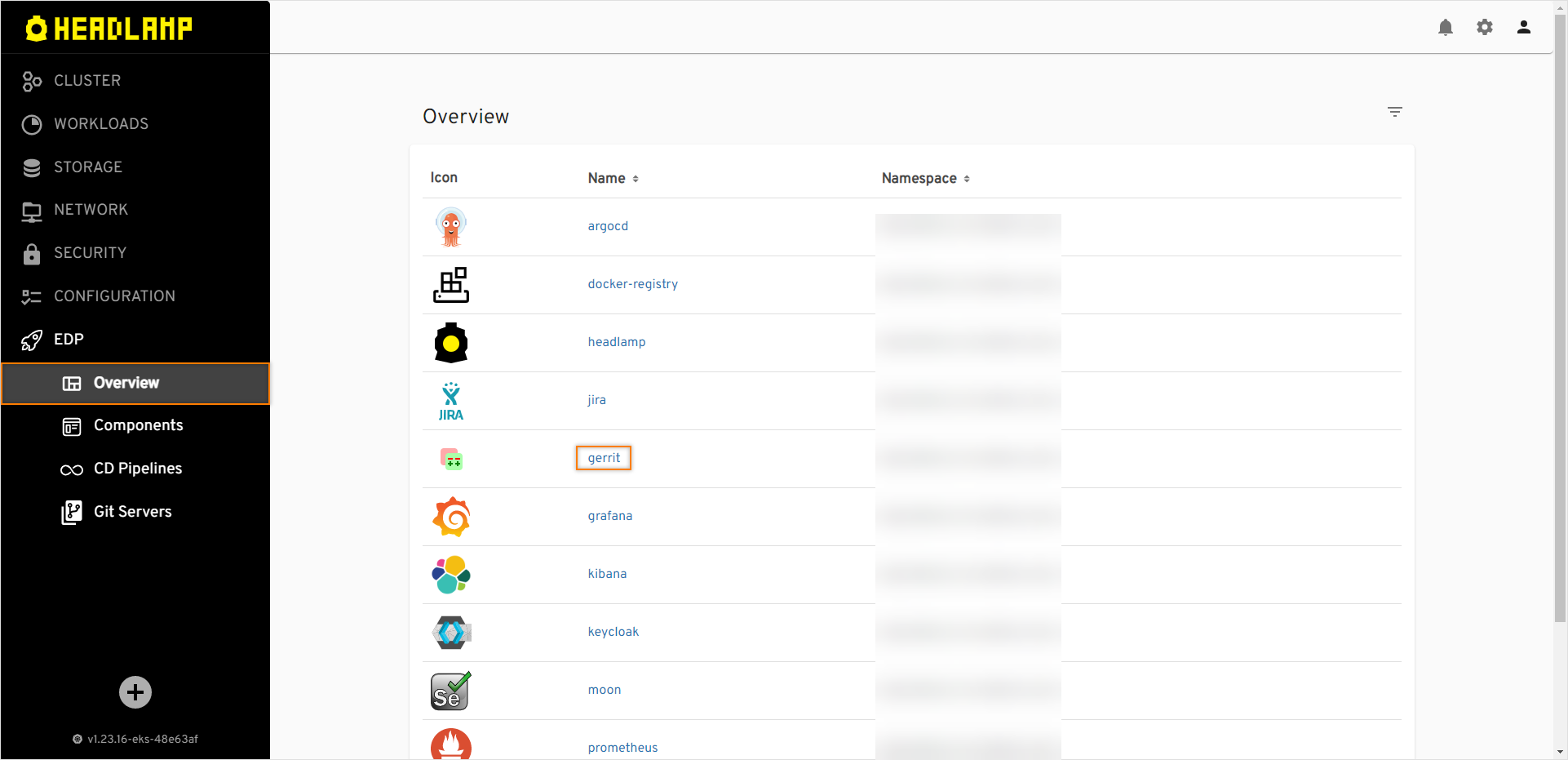
Navigate to
EDP Portal->EDP->Overview, and push the Gerrit link: -
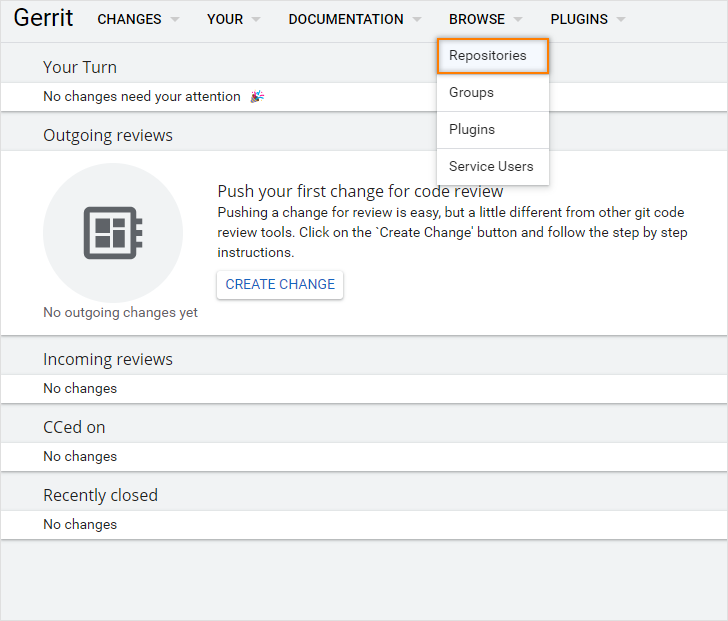
Log in to Gerrit UI, select
Repositoriesand selectes-usageproject: -
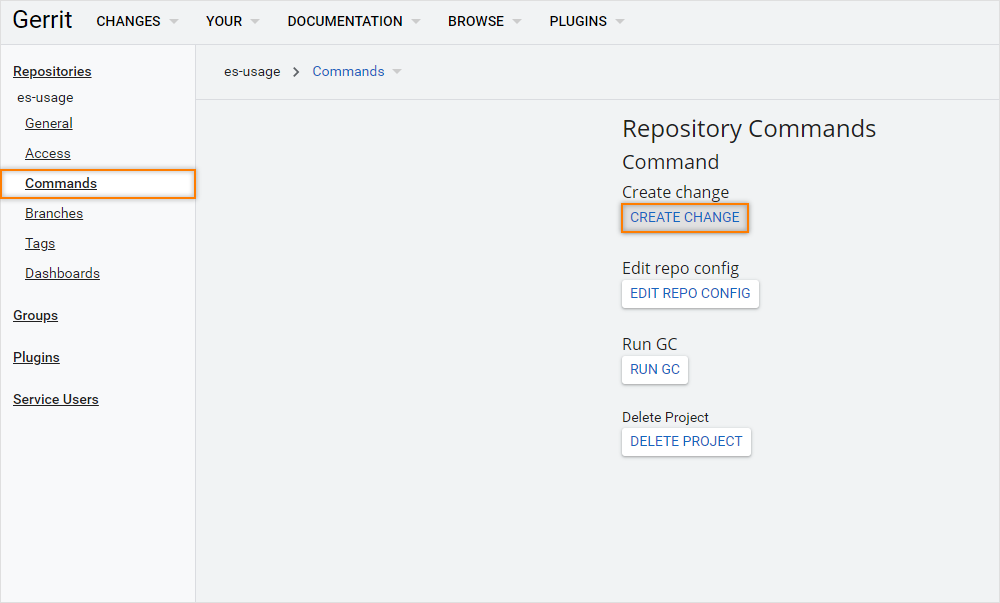
In the
Commandssection of the project, push theCreate Changebutton: -
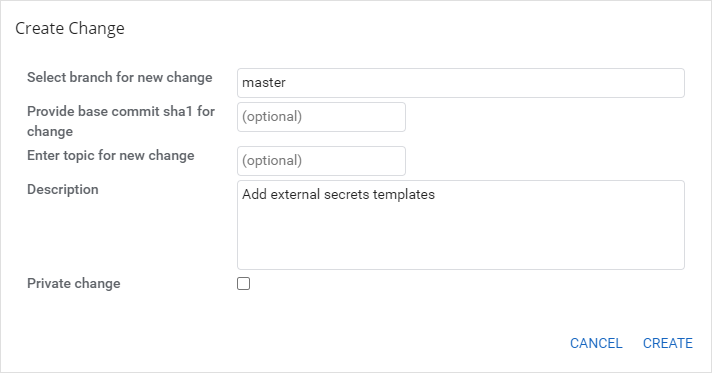
In the
Create Changedialog, provide the branchmasterand fill in theDescription(commit message) field and push theCreatebutton: -
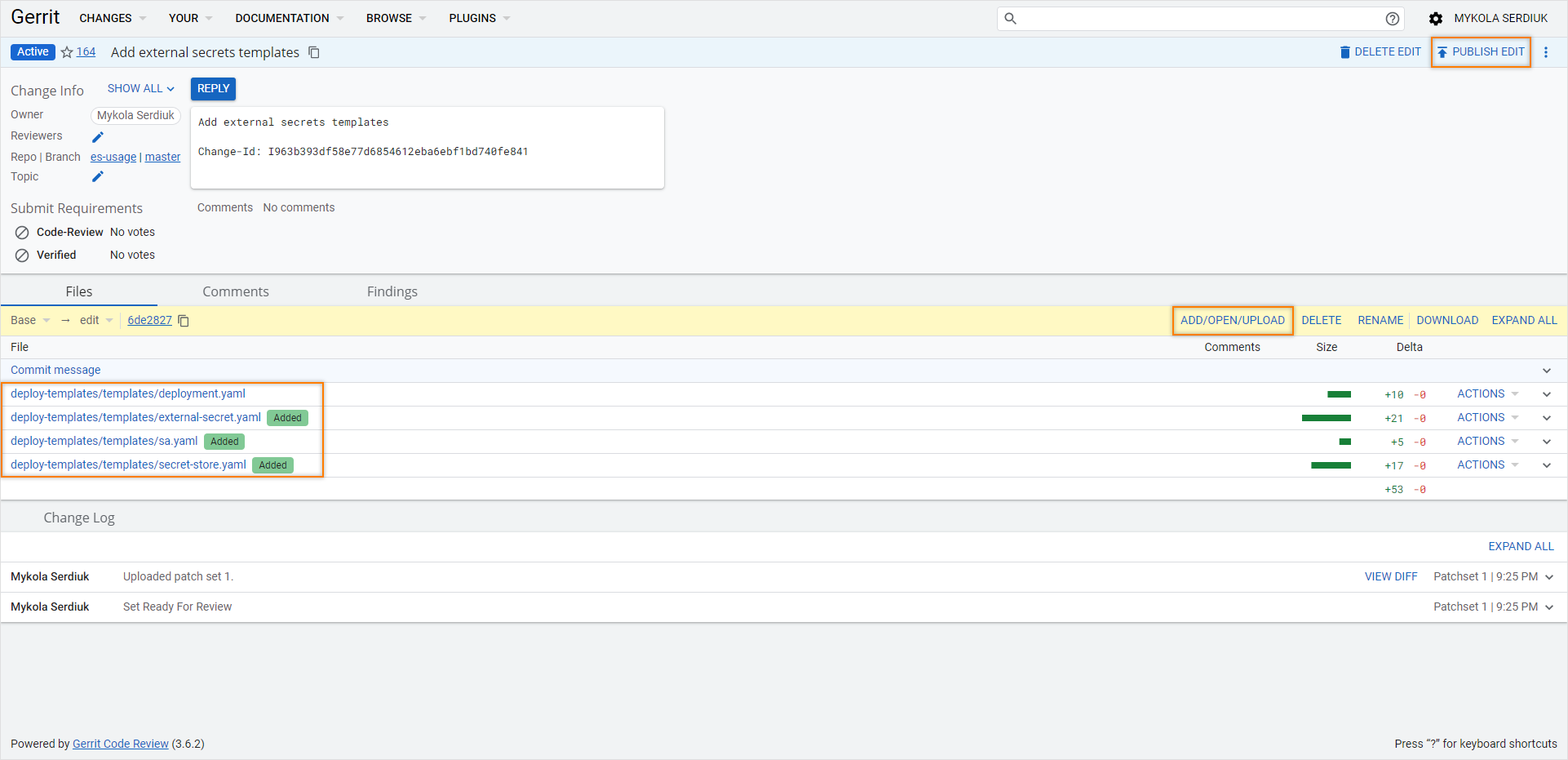
Push the
Editbutton of the merge request and then theADD/OPEN/UPLOADbutton and add files:Once the file menu is opened, and click
SAVEafter editing each of the files:-
deploy-templates/templates/sa.yaml:
-
deploy-templates/templates/secret-store.yaml:
-
deploy-templates/templates/external-secret.yaml:
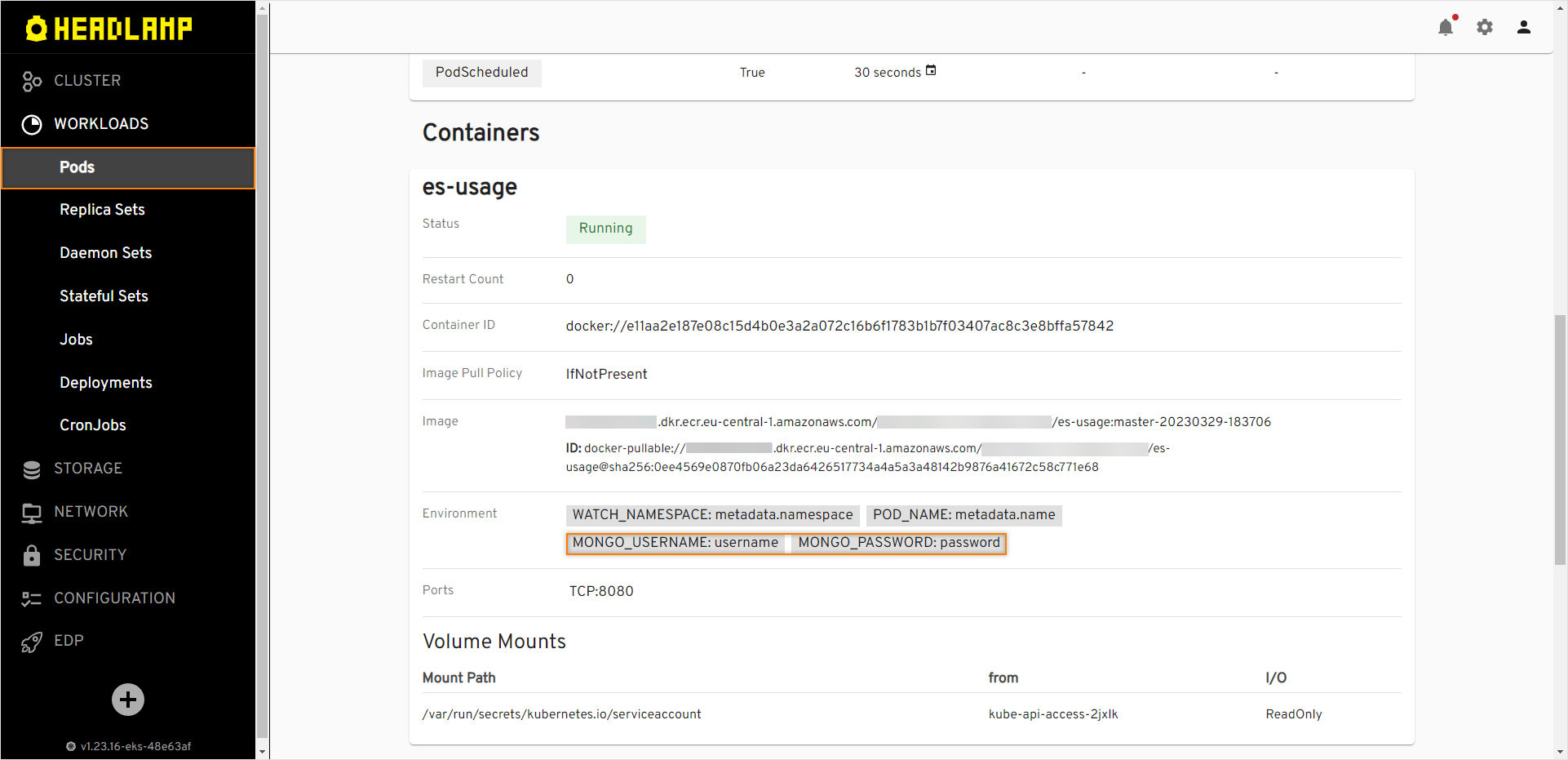
apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata: name: mongo # target secret name namespace: demo-deploy-sit # target namespace spec: refreshInterval: 1h secretStoreRef: kind: SecretStore name: demo data: - secretKey: username # target value property remoteRef: key: mongo # remote secret key property: username # value will be fetched from this field - secretKey: password # target value property remoteRef: key: mongo # remote secret key property: password # value will be fetched from this field -
deploy-templates/templates/deployment.yaml. Add the environment variable for mongodb to the existing deployment configuration that used the secret:
-
-
Push the
Publish Editbutton. -
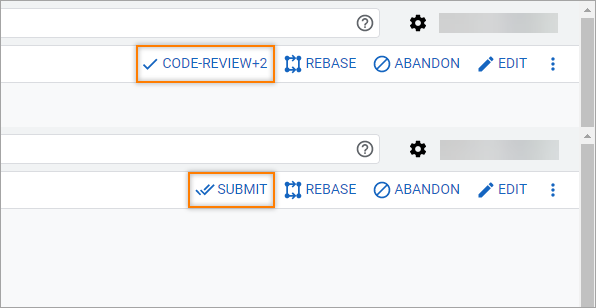
As soon as review pipeline finished, and you get
Verified +1from CI, you are ready for review. ClickMark as Active->Code-Review +2->Submit:
Deploy Application⚓︎
Deploy the application by following the steps provided below:
-
When build pipeline is finished, navigate to
EDP Portal->EDP->CD-Pipelineand selectdeploypipeline. -
Deploy the initial version of the application to the SIT environment:
- Select the
sitstage from the Stages tab; - In the
Image stream version, select latest version and push theDeploybutton.
- Select the
-
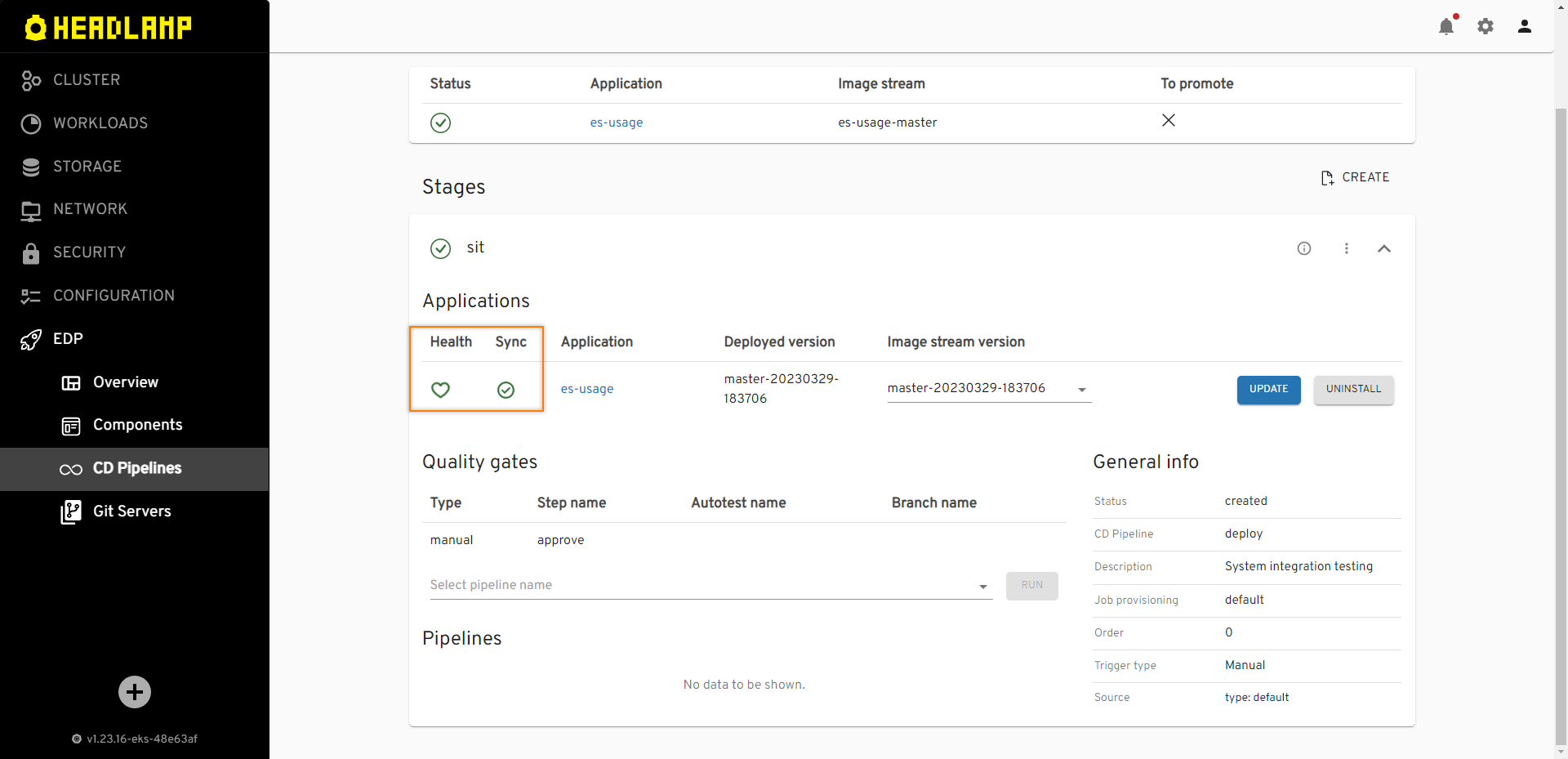
Ensure application status is
HealthyandSynced:
Check Application Status⚓︎
To ensure the application is deployed successfully, do the following:
-
Check that the resources are deployed:
-
In the top right corner, enter the
Cluster settingsand adddemo-deploy-sitto theAllowed namespace. -
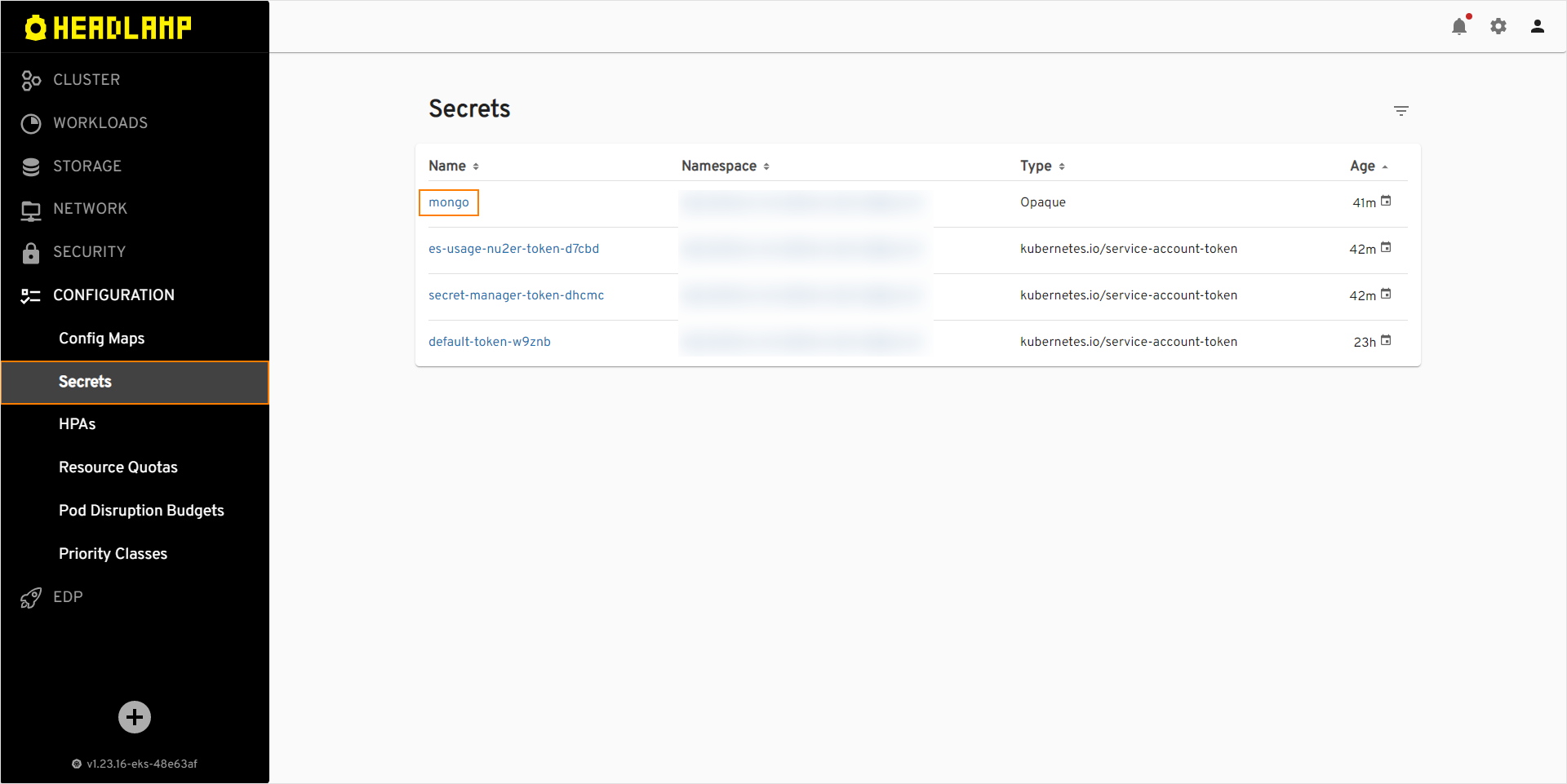
Navigate
EDP Portal->Configuration->Secretsand ensure that secret was created: -
Navigate
EDP Portal->Workloads->Podsand select deployed application: