SonarQube Integration⚓︎
This documentation guide provides comprehensive instructions for integrating SonarQube with the EPAM Delivery Platform.
Info
In EDP release 3.5, we have changed the deployment strategy for the sonarqube-operator component, now it is not installed by default. The sonarURL parameter management has been transferred from the values.yaml file to Kubernetes secrets.
Prerequisites⚓︎
Before proceeding, ensure that you have the following prerequisites:
Installation⚓︎
To install SonarQube with pre-defined templates, use the sonar-operator installed via Cluster Add-Ons approach.
Configuration⚓︎
To establish robust authentication and precise access control, generating a SonarQube token is essential. This token is a distinct identifier, enabling effortless integration between SonarQube and EDP. To generate the SonarQube token, proceed with the following steps:
-
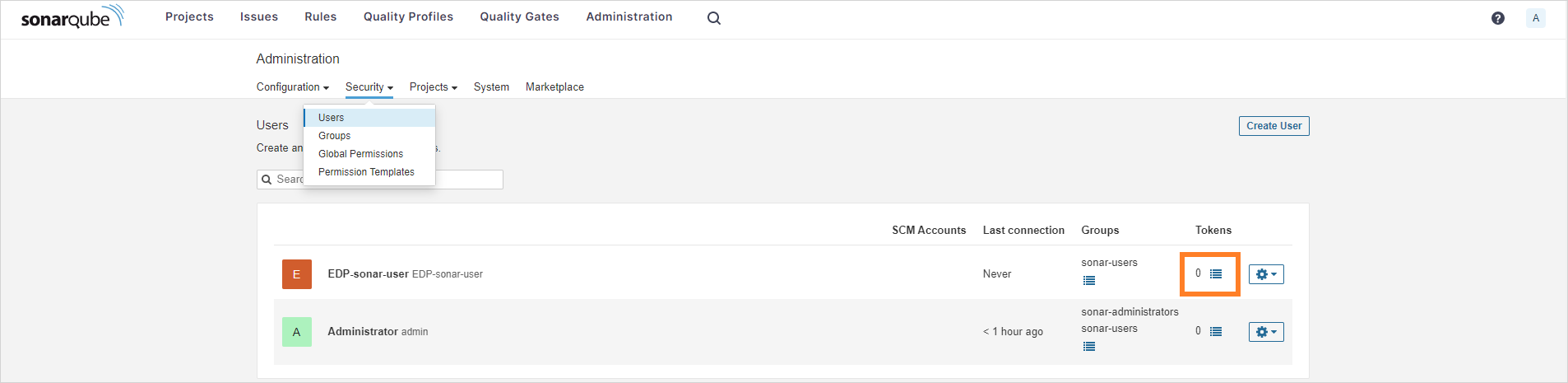
Open the SonarQube UI and navigate to
Administration->Security->User. Create a new user or select an existing one. Click theOptions Listicon to create a token: -
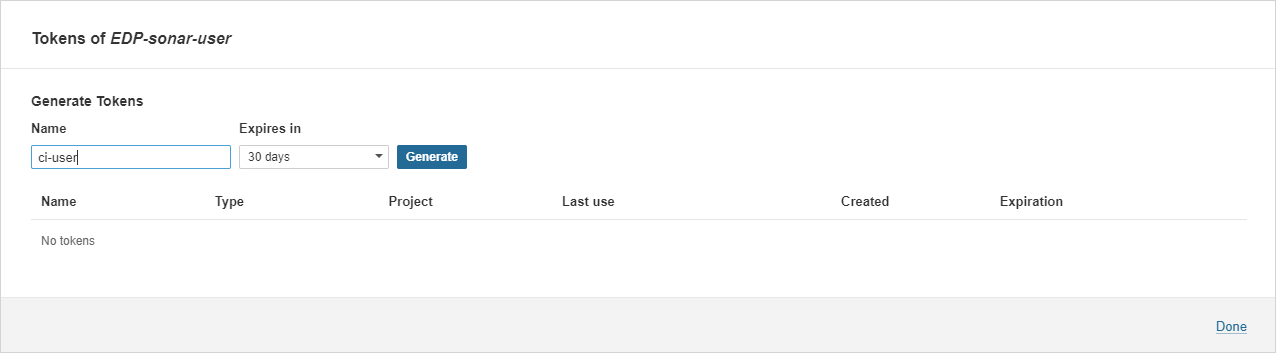
Type the
ci-userusername, define an expiration period, and click theGeneratebutton to create the token: -
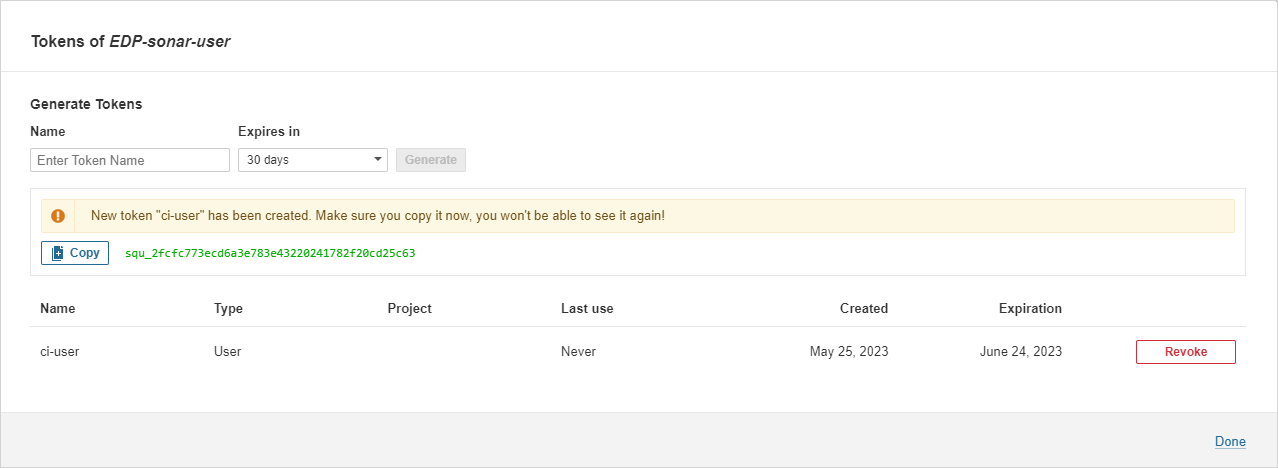
Click the
Copybutton to copy the generated<Sonarqube-token>: -
Provision secrets using Manifest, EDP Portal or with the externalSecrets operator:
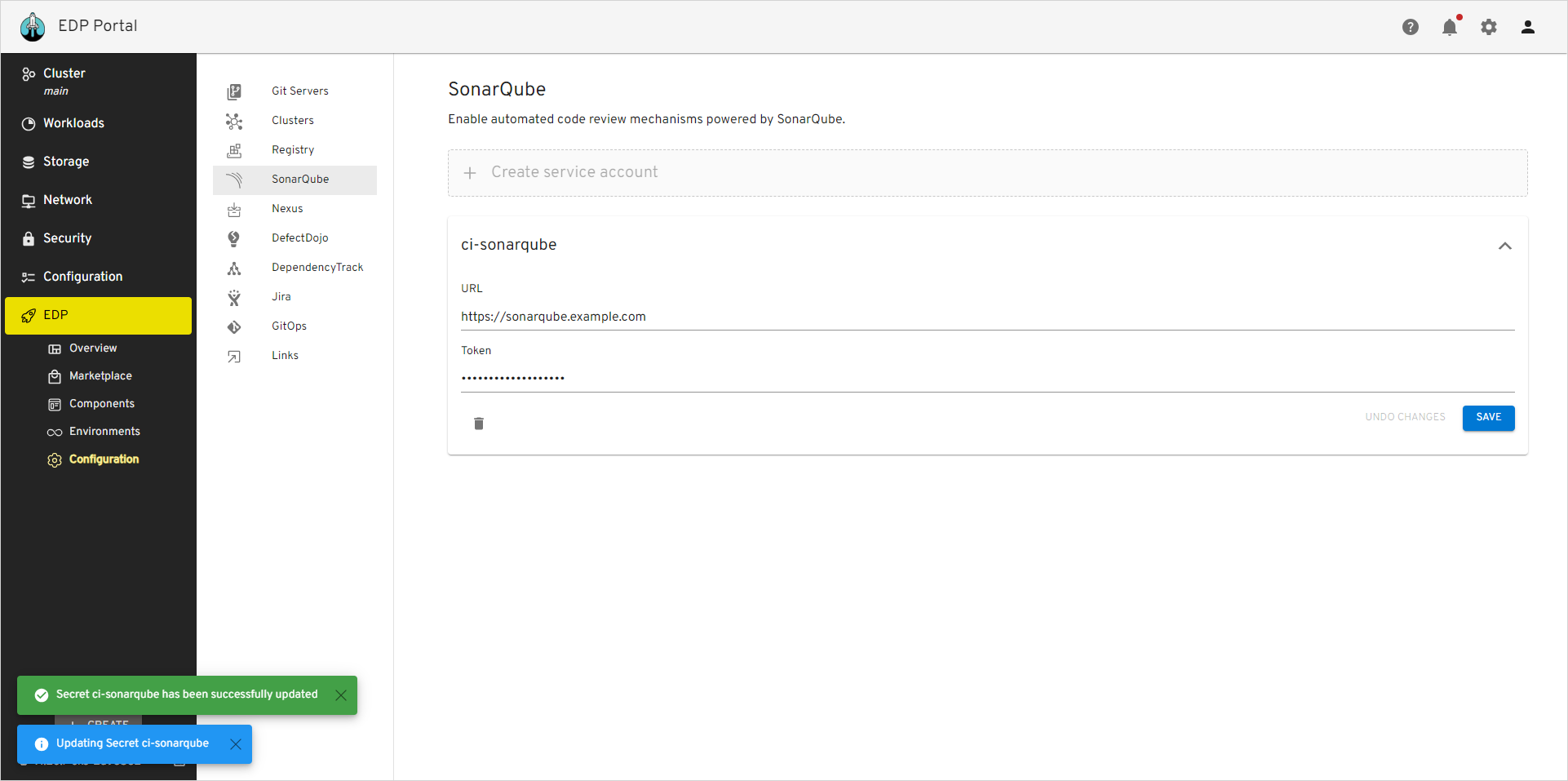
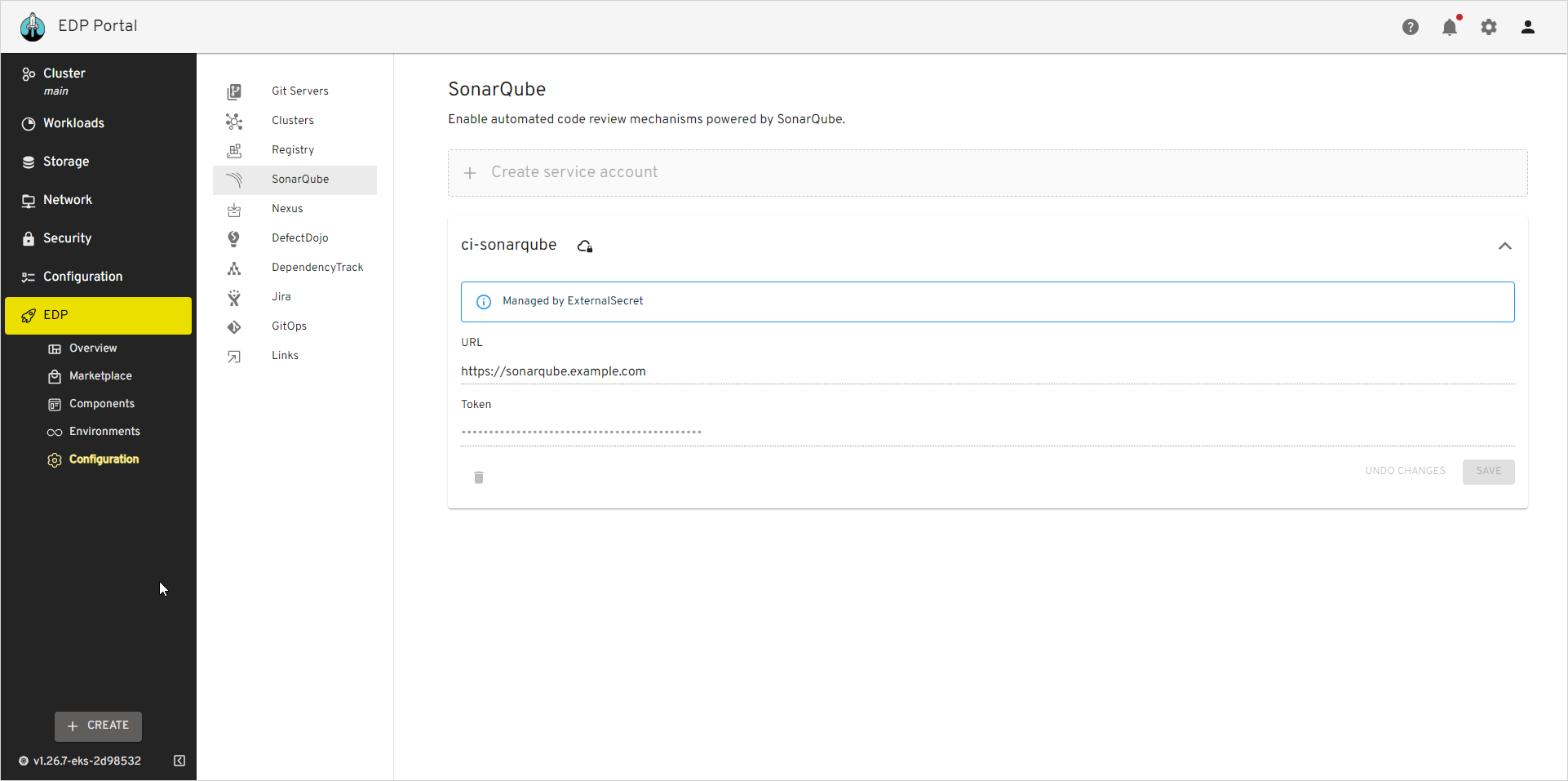
Go to EDP Portal -> EDP -> Configuration -> SonarQube. Update or fill in the URL and Token fields and click the Save button:
Go to EDP Portal -> EDP -> Configuration -> SonarQube and see the Managed by External Secret message:
More details about External Secrets Operator integration can be found in the External Secrets Operator Integration page.