Install via Helmfile⚓︎
This article provides the instruction on how to deploy EDP and components in Kubernetes using Helmfile that is intended for deploying Helm charts. Helmfile templates are available in GitHub repository.
Important
The Helmfile installation method for EPAM Delivery Platform (EDP) is currently not actively maintained. We strongly recommend exploring alternative installation options for the most up-to-date and well-supported deployment experience. You may consider using the Add-Ons approach or opting for installation via the AWS Marketplace to ensure a reliable and secure deployment of EDP.
Prerequisites⚓︎
The following tools and plugins must be installed:
- Kubectl version 1.23.0;
- Helm version 3.10.0+;
- Helmfile version 0.144.0;
- Helm diff plugin version 3.6.0.
Helmfile Structure⚓︎
- The
envs/common.yamlfile contains the specification for environments pattern, list of helm repositories from which it is necessary to fetch the helm charts and additional Helm parameters. - The
envs/platform.yamlfile contains global parameters that are used in various Helmfiles. - The
releases/envs/contains symbol links to environments files. - The
releases/*.yamlfile contains description of parameters that is used when deploying a Helm chart. - The
helmfile.yamlfile defines components to be installed by defining a path to Helm releases files. - The
envs/ci.yamlfile contains stub parameters for CI linter. - The
test/lint-ci.shscript for running CI linter with debug loglevel and stub parameters. - The
resources/*.yamlfile contains additional resources for the OpenShift platform.
Operate Helmfile⚓︎
Before applying the Helmfile, please fill in the global parameters in the envs/platform.yaml (check the examples in the envs/ci.yaml) and releases/*.yaml files for every Helm deploy.
Pay attention to the following recommendations while working with the Helmfile:
- To launch Lint, run the
test/lint-ci.shscript.
- Display the difference between the deployed and environment state (
helm diff):helmfile --environment platform -f helmfile.yaml diff
- Apply the deployment:
helmfile --selector component=ingress --environment platform -f helmfile.yaml apply
- Modify the deployment and apply the changes:
helmfile --selector component=ingress --environment platform -f helmfile.yaml sync
- To deploy the components according to the label, use the selector to target a subset of releases when running the Helmfile. It can be useful for large Helmfiles with the releases that are logically grouped together. For example, to display the difference only for the
nginx-ingressfile, use the following command:helmfile --selector component=ingress --environment platform -f helmfile.yaml diff
- To destroy the release, run the following command:
helmfile --selector component=ingress --environment platform -f helmfile.yaml destroy
Deploy Components⚓︎
Using the Helmfile, the following components can be installed:
- NGINX Ingress Controller
- Keycloak
- EPAM Delivery Platform
- Argo CD
- External Secrets Operator
- DefectDojo
- Moon
- ReportPortal
- Kiosk
- Monitoring stack, included Prometheus, Alertmanager, Grafana, PrometheusOperator
- Logging ELK stack, included Elasticsearch, Fluent-bit, Kibana
- Logging Grafana/Loki stack, included Grafana, Loki, Promtail, Logging Operator, Logging Operator Logging
Deploy NGINX Ingress Controller⚓︎
Info
Skip this step for the OpenShift platform, because it has its own Ingress Controller.
To install NGINX Ingress controller, follow the steps below:
-
In the
releases/nginx-ingress.yamlfile, set theproxy-real-ip-cidrparameter according to the value with AWS VPC IPv4 CIDR. -
Install NGINX Ingress controller:
helmfile --selector component=ingress --environment platform -f helmfile.yaml apply
Deploy Keycloak⚓︎
Keycloak requires a database deployment, so it has two charts: releases/keycloak.yaml and releases/postgresql-keycloak.yaml.
To install Keycloak, follow the steps below:
-
Create a
securitynamespace:Note
For the OpenShift users:
This namespace is also indicated asusersin the following customSecurityContextConstraintsresources:resources/keycloak-scc.yamlandresources/postgresql-keycloak-scc.yaml. Change the namespace name when using a custom namespace. -
Create PostgreSQL admin secret:
kubectl -n security create secret generic keycloak-postgresql \ --from-literal=password=<postgresql_password> \ --from-literal=postgres-password=<postgresql_postgres_password> -
In the
envs/platform.yamlfile, set thednsWildCardparameter. -
Create Keycloak admin secret:
kubectl -n security create secret generic keycloak-admin-creds \ --from-literal=username=<keycloak_admin_username> \ --from-literal=password=<keycloak_admin_password> -
Install Keycloak:
helmfile --selector component=sso --environment platform -f helmfile.yaml apply
Deploy External Secrets Operator⚓︎
To install External Secrets Operator, follow the steps below:
Deploy Kiosk⚓︎
To install Kiosk, follow the steps below:
Deploy EPAM Delivery Platform⚓︎
To install EDP, follow the steps below:
-
Create a
platformnamespace:kubectl create namespace platform -
For EDP, it is required to have Keycloak access to perform the integration. Create a secret with the user and password provisioned in the step 2 of the Keycloak Configuration section.
kubectl -n platform create secret generic keycloak \ --from-literal=username=<username> \ --from-literal=password=<password> -
In the
envs/platform.yamlfile, set theedpNameandkeycloakEndpointparameters. -
In the
releases/edp-install.yamlfile, check and fill in all values. -
Install EDP:
helmfile --selector component=edp --environment platform -f helmfile.yaml apply
Deploy Argo CD⚓︎
Before Argo CD deployment, install the following tools:
To install Argo CD, follow the steps below:
-
Install Argo CD:
For the OpenShift users:
When using a custom namespace for Argo CD, the `argocd` namespace is also indicated as `users` in the `resources/argocd-scc.yaml` custom `SecurityContextConstraints` resource. Change it there as well. -
Update the
argocd-secretsecret in the Argo CD namespace by providing the correct Keycloak client secret (oidc.keycloak.clientSecret) with the value from thekeycloak-client-argocd-secretsecret in EDP namespace. Then restart the deployment:
Deploy DefectDojo⚓︎
Prerequisites
- Before DefectDojo deployment,first make sure to have the Keycloak configuration.
Info
It is also possible to install DefectDojo via Helm Chart. For details, please refer to the Install DefectDojo page.
To install DefectDojo via Helmfile, follow the steps below:
-
Create a DefectDojo namespace:
For the OpenShift users:
This namespace is also indicated as
usersin theresources/defectdojo-scc.yamlcustomSecurityContextConstraintsresource. Change it when using a custom namespace. Also, change the namespace in theresources/defectdojo-route.yamlfile. -
Modify the
hostinresources/defectdojo-route.yaml(only for OpenShift). -
Create a PostgreSQL admin secret:
kubectl -n defectdojo create secret generic defectdojo-postgresql-specific \ --from-literal=postgresql-password=<postgresql_password> \ --from-literal=postgresql-postgres-password=<postgresql_postgres_password>Note
The
postgresql_passwordandpostgresql_postgres_passwordpasswords must be 16 characters long. -
Create a RabbitMQ admin secret:
kubectl -n defectdojo create secret generic defectdojo-rabbitmq-specific \ --from-literal=rabbitmq-password=<rabbitmq_password> \ --from-literal=rabbitmq-erlang-cookie=<rabbitmq_erlang_cookie>Note
The
rabbitmq_passwordpassword must be 10 characters long.The
rabbitmq_erlang_cookiepassword must be 32 characters long. -
Create a DefectDojo admin secret:
kubectl -n defectdojo create secret generic defectdojo \ --from-literal=DD_ADMIN_PASSWORD=<dd_admin_password> \ --from-literal=DD_SECRET_KEY=<dd_secret_key> \ --from-literal=DD_CREDENTIAL_AES_256_KEY=<dd_credential_aes_256_key> \ --from-literal=METRICS_HTTP_AUTH_PASSWORD=<metric_http_auth_password>Note
The
dd_admin_passwordpassword must be 22 characters long.The
dd_secret_keypassword must be 128 characters long.The
dd_credential_aes_256_keypassword must be 128 characters long.The
metric_http_auth_passwordpassword must be 32 characters long. -
Create a Keycloak client secret for DefectDojo:
Note
The
keycloak_client_secretvalue received from:edpName-main realm -> clients -> defectdojo -> Credentials -> Client secret -
In the
envs/platform.yamlfile, set thednsWildCardparameter. -
In the releases/defectdojo.yaml file, check and fill in all values.
-
Install DefectDojo:
Deploy ReportPortal⚓︎
Info
It is also possible to install ReportPortal via Helm Chart. For details, please refer to the Install ReportPortal page.
ReportPortal requires third-party deployments: RabbitMQ, ElasticSearch, PostgreSQL, MinIO.
To install third-party resources, follow the steps below:
-
Create a RabbitMQ admin secret:
kubectl -n report-portal create secret generic reportportal-rabbitmq-creds \ --from-literal=rabbitmq-password=<rabbitmq_password> \ --from-literal=rabbitmq-erlang-cookie=<rabbitmq_erlang_cookie>Warning
The
rabbitmq_passwordpassword must be 10 characters long.The
rabbitmq_erlang_cookiepassword must be 32 characters long. -
Create a PostgreSQL admin secret:
kubectl -n report-portal create secret generic reportportal-postgresql-creds \ --from-literal=postgresql-password=<postgresql_password> \ --from-literal=postgresql-postgres-password=<postgresql_postgres_password>Warning
The
postgresql_passwordandpostgresql_postgres_passwordpasswords must be 16 characters long. -
Create a MinIO admin secret:
-
In the
envs/platform.yamlfile, set thednsWildCardandedpNameparameters.For the OpenShift users:
The namespace is also indicated as
usersin the following customSecurityContextConstraintsresources:resources/report-portal-elasticsearch-scc.yamlandresources/report-portal-third-party-resources-scc.yaml. Change the namespace name when using a custom namespace. -
Install third-party resources:
-
After the rabbitmq pod gets the status Running, you need to configure the RabbitMQ memory threshold
To install ReportPortal via Helmfile, follow the steps below:
For the OpenShift users:
- The namespace is also indicated as
usersin theresources/report-portal-reportportal-scc.yamlcustomSecurityContextConstraintsresource. Change it when using a custom namespace. - Change the namespace in the following files:
resources/report-portal-gateway/gateway-config-cm,resources/report-portal-gateway/gateway-deployment,resources/report-portal-gateway/gateway-route, andresources/report-portal-gateway/gateway-service. - Modify the
hostinresources/report-portal-gateway/gateway-route
Note
For user access: default/1q2w3e
For admin access: superadmin/erebus
Please refer to the ReportPortal.io page for details.
Deploy Moon⚓︎
Moon is a browser automation solution compatible with Selenium, Cypress, Playwright, and Puppeteer using Kubernetes or Openshift to launch browsers.
Note
Aerokube/Moon does not require third-party deployments.
Follow the steps below to deploy Moon:
-
Use the following command to install Moon:
-
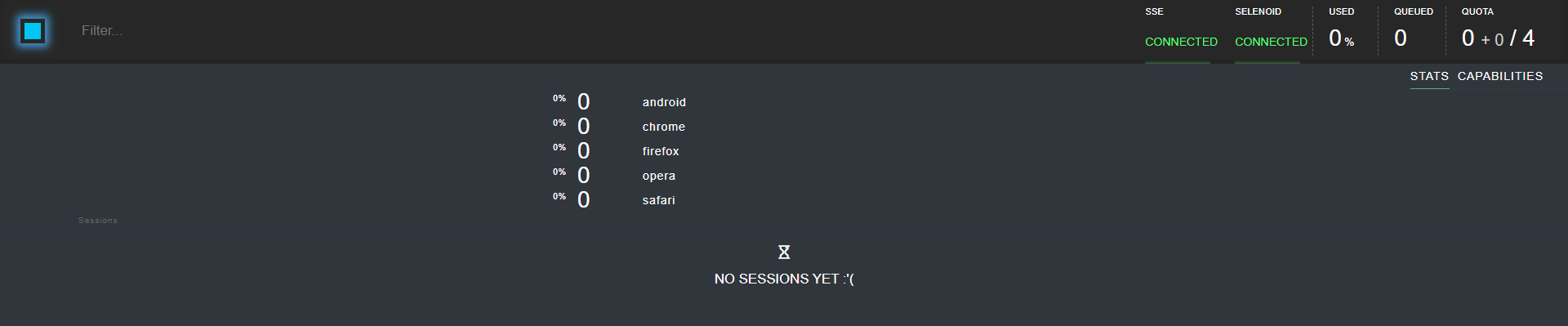
After the installation, open the Ingress Dashboard and check that
SELENOIDandSSEhave theCONNECTEDstatus. -
In Moon, use the following command with the Ingress rule, for example,
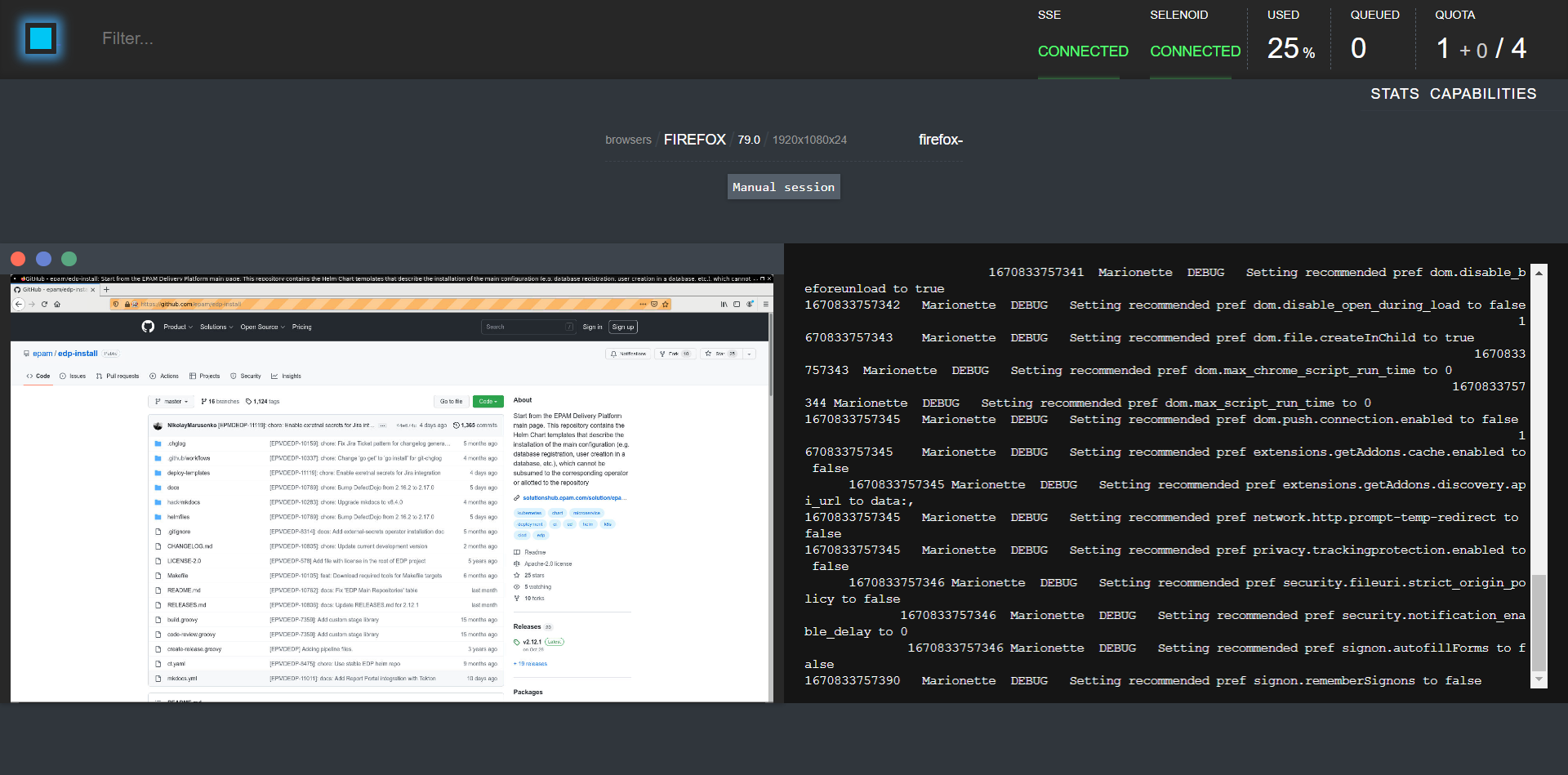
wd/hub:curl -X POST 'http://<INGRESS_LINK>/wd/hub/session' -d '{ "desiredCapabilities":{ "browserName":"firefox", "version": "79.0", "platform":"ANY", "enableVNC": true, "name": "edp", "sessionTimeout": "480s" } }'See below the list of Moon Dashboard Ingress rules:
After using the command above, the container will start, and the VNC viewer will be displayed on the Moon Dashboard:
Deploy Monitoring⚓︎
The monitoring stack includes Grafana, Prometheus, Alertmanager, and Karma-dashboard. To deploy it follow the steps:
-
Generate a token for Keycloak client:
Note
The token must be 32-character and include alphabetic and numeric symbols. For example, use the following command:
-
Create a custom resource for the Keycloak client:
-
Run command:
Deploy Logging⚓︎
To install Elasticsearch, Kibana and Fluentbit, run command:
To install Grafana, Loki, Promtail, follow the steps below:
-
Make sure that appropriate resources are created:
- Secret for the Keycloak client
- Secret for the Grafana
-
Create a custom resource for the Keycloak client:
View: keycloak_client
-
Run command: