Install Keycloak⚓︎
Inspect the prerequisites and the main steps to perform for installing Keycloak.
Info
The installation process below is given for a Kubernetes cluster. The steps that differ for an OpenShift cluster are indicated in the warnings blocks.
Prerequisites⚓︎
- Kubectl version 1.23.0 is installed. Please refer to the Kubernetes official website for details.
- Helm version 3.10.0+ is installed. Please refer to the Helm page on GitHub for details.
Info
EDP team is using a Keycloakx helm chart from the codecentric repository, but other repositories can be used as well (e.g. Bitnami). Before installing Keycloak, it is necessary to install a PostgreSQL database.
Info
It is also possible to install Keycloak using the cluster add-ons. For details, please refer to the Install via Add-Ons page.
PostgreSQL Installation⚓︎
To install PostgreSQL, follow the steps below:
-
Check that a security namespace is created. If not, run the following command to create it:
kubectl create namespace securityWarning
On the OpenShift platform, apply the
SecurityContextConstraintsresource. Change the namespace in theuserssection if required.View: keycloak-scc.yaml
allowHostDirVolumePlugin: false allowHostIPC: false allowHostNetwork: false allowHostPID: false allowHostPorts: false allowPrivilegeEscalation: true allowPrivilegedContainer: false allowedCapabilities: null apiVersion: security.openshift.io/v1 allowedFlexVolumes: [] defaultAddCapabilities: [] fsGroup: type: MustRunAs ranges: - min: 999 max: 65543 groups: [] kind: SecurityContextConstraints metadata: annotations: "helm.sh/hook": "pre-install" name: keycloak priority: 1 readOnlyRootFilesystem: false requiredDropCapabilities: - KILL - MKNOD - SETUID - SETGID runAsUser: type: MustRunAsRange uidRangeMin: 1 uidRangeMax: 65543 seLinuxContext: type: MustRunAs supplementalGroups: type: RunAsAny users: - system:serviceaccount:security:keycloakx volumes: - configMap - downwardAPI - emptyDir - persistentVolumeClaim - projected - secretView: postgresql-keycloak-scc.yaml
allowHostDirVolumePlugin: false allowHostIPC: false allowHostNetwork: false allowHostPID: false allowHostPorts: false allowPrivilegeEscalation: true allowPrivilegedContainer: false allowedCapabilities: null apiVersion: security.openshift.io/v1 allowedFlexVolumes: [] defaultAddCapabilities: [] fsGroup: type: MustRunAs ranges: - min: 999 max: 65543 groups: [] kind: SecurityContextConstraints metadata: annotations: "helm.sh/hook": "pre-install" name: postgresql-keycloak priority: 1 readOnlyRootFilesystem: false requiredDropCapabilities: - KILL - MKNOD - SETUID - SETGID runAsUser: type: MustRunAsRange uidRangeMin: 1 uidRangeMax: 65543 seLinuxContext: type: MustRunAs supplementalGroups: type: RunAsAny users: - system:serviceaccount:security:default volumes: - configMap - downwardAPI - emptyDir - persistentVolumeClaim - projected - secret -
Create PostgreSQL admin secret:
-
Add a helm chart repository:
-
Install PostgreSQL v15.2.0 using bitnami/postgresql Helm chart v12.1.15:
Info
The PostgreSQL can be deployed in production ready mode. For example, it may include multiple replicas, persistent storage, autoscaling, and monitoring. For details, please refer to the official Chart documentation.
helm install postgresql bitnami/postgresql \ --version 12.1.15 \ --values values.yaml \ --namespace securityCheck out the values.yaml file sample of the PostgreSQL customization:
View: values.yaml
Keycloak Installation⚓︎
To install Keycloak, follow the steps below:
-
Use
securitynamespace from the PostgreSQL installation. -
Add a chart repository:
-
Create Keycloak admin secret:
-
Install Keycloak 20.0.3 using codecentric/keycloakx Helm chart:
Info
Keycloak can be deployed in production ready mode. For example, it may include multiple replicas, persistent storage, autoscaling, and monitoring. For details, please refer to the official Chart documentation.
helm install keycloakx codecentric/keycloakx \ --version 2.2.1 \ --values values.yaml \ --namespace securityCheck out the values.yaml file sample of the Keycloak customization:
View: values.yaml
replicas: 1 # Deploy the latest version image: tag: "20.0.3" # start: create OpenShift realm which is required by EDP extraInitContainers: | - name: realm-provider image: busybox imagePullPolicy: IfNotPresent command: - sh args: - -c - | echo '{"realm": "openshift","enabled": true}' > /opt/keycloak/data/import/openshift.json volumeMounts: - name: realm mountPath: /opt/keycloak/data/import # The following parameter is unrecommended to expose. Exposed health checks lead to an unnecessary attack vector. health: enabled: false # The following parameter is unrecommended to expose. Exposed metrics lead to an unnecessary attack vector. metrics: enabled: false extraVolumeMounts: | - name: realm mountPath: /opt/keycloak/data/import extraVolumes: | - name: realm emptyDir: {} command: - "/opt/keycloak/bin/kc.sh" - "--verbose" - "start" - "--auto-build" - "--http-enabled=true" - "--http-port=8080" - "--hostname-strict=false" - "--hostname-strict-https=false" - "--spi-events-listener-jboss-logging-success-level=info" - "--spi-events-listener-jboss-logging-error-level=warn" - "--import-realm" extraEnv: | - name: KC_PROXY value: "passthrough" - name: KEYCLOAK_ADMIN valueFrom: secretKeyRef: name: keycloak-admin-creds key: username - name: KEYCLOAK_ADMIN_PASSWORD valueFrom: secretKeyRef: name: keycloak-admin-creds key: password - name: JAVA_OPTS_APPEND value: >- -XX:+UseContainerSupport -XX:MaxRAMPercentage=50.0 -Djava.awt.headless=true -Djgroups.dns.query={{ include "keycloak.fullname" . }}-headless # This block should be uncommented if you install Keycloak on Kubernetes ingress: enabled: true annotations: kubernetes.io/ingress.class: nginx ingress.kubernetes.io/affinity: cookie # The following parameter is unrecommended to expose. Admin paths lead to an unnecessary attack vector. console: enabled: false rules: - host: keycloak.<ROOT_DOMAIN> paths: - path: '{{ tpl .Values.http.relativePath $ | trimSuffix "/" }}/' pathType: Prefix # This block should be uncommented if you set Keycloak to OpenShift and change the host field # route: # enabled: false # # Path for the Route # path: '/' # # Host name for the Route # host: "keycloak.<ROOT_DOMAIN>" # # TLS configuration # tls: # enabled: true resources: limits: memory: "2048Mi" requests: cpu: "50m" memory: "512Mi" # Check database readiness at startup dbchecker: enabled: true database: vendor: postgres existingSecret: keycloak-postgresql hostname: postgresql port: 5432 username: admin database: keycloak
Configuration⚓︎
To prepare Keycloak for integration with EDP, follow the steps below:
-
Ensure that the
openshiftrealm is created. -
Create the
edp_<EDP_PROJECT>user and set the password in theMasterrealm.Note
This user should be used by EDP to access Keycloak. Please refer to the Install EDP page for details.
-
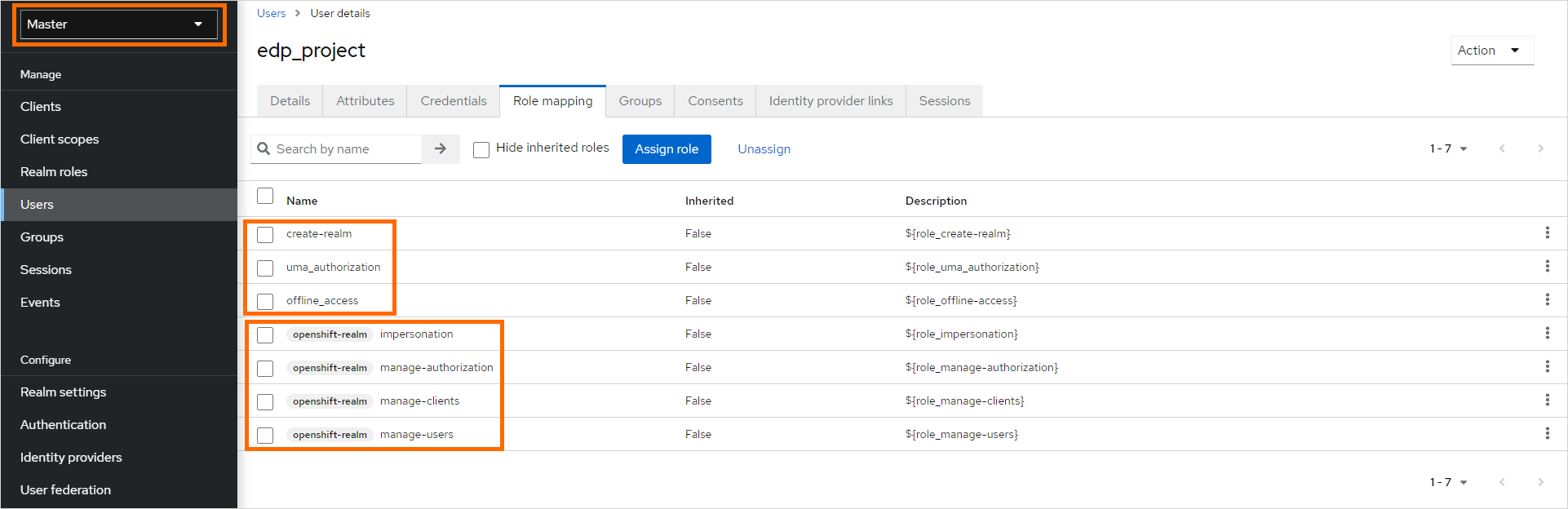
In the
Role Mappingtab, assign the proper roles to the user:-
Realm Roles:
- create-realm,
- offline_access,
- uma_authorization
-
Client Roles
openshift-realm:- impersonation,
- manage-authorization,
- manage-clients,
- manage-users
-