External Secrets Operator Integration⚓︎
External Secrets Operator (ESO) can be integrated with EDP.
There are multiple Secrets Providers that can be used within ESO. EDP is integrated with two major providers:
EDP uses various secrets to integrate various applications. Below is a list of secrets that are used in the EPAM Delivery Platform and their description. All the secrets are encoded in Base64 format.
| Secret Name | Fields | Description | Used by |
|---|---|---|---|
| keycloak | username password | Username and password with specific rights for EDP tenant in Keycloak | keycloak-operator |
| ci-defectdojo | token url | DefectDojo token DefectDojo URL | edp-tekton |
| kaniko-docker-config | .dockerconfigjson | Serialized JSON that follows docker config patterns | edp-tekton |
| regcred | .dockerconfigjson | Serialized JSON that follows docker config patterns | cd-pipeline-operator |
| ci-github | id_rsa token secretString | Private key from github repo API token Random string | edp-tekton |
| ci-gitlab | id_rsa token secretString | Private key from gitlab repo API token Random string | edp-tekton |
| ci-jira | username password | Jira username Jira password | edp-codebase-operator |
| ci-sonarqube | token url | SonarQube token SonarQube URL | edp-tekton |
| ci-nexus | username password url | Nexus username Nexus password Nexus URL | edp-tekton |
| ci-dependency-track | token url | Dependency-Track token Dependency-Track URL | edp-tekton |
| oauth2-proxy-cookie-secret | cookie-secret | Secret key for oauth2-proxy | edp-install |
| keycloak-client-headlamp-secret | clientSecret | Secret key for keycloak client | keycloak-operator |
| ci-argocd | token url | Argo CD token Argo CD URL | edp-tekton |
EDP Core Secrets⚓︎
The list below represents the baseline required for full operation within EDP:
- kaniko-docker-config: Used for pushing docker images to a specific registry.
- ci-sonarqube: Used in the CI process for SonarQube integration.
- ci-nexus: Used for pushing artifacts to the Nexus storage.
These secrets are mandatory for Tekton pipelines to work properly.
Kubernetes Provider⚓︎
All secrets are stored in Kubernetes in pre-defined namespaces. EDP suggests using the following approach for secrets management:
EDP_NAMESPACE-vault, where EDP_NAMESPACE is a name of the namespace where EDP is deployed, such asedp-vault. This namespace is used by EDP platform. Access to secrets in theedp-vaultis permitted only forEDP Administrators.
EDP_NAMESPACE-cicd-vault, where EDP_NAMESPACE is a name of the namespace where EDP is deployed, such asedp-cicd-vault. Development team uses access to secrets in theedp-cicd-vaultfor microservices development.
See a diagram below for more details:
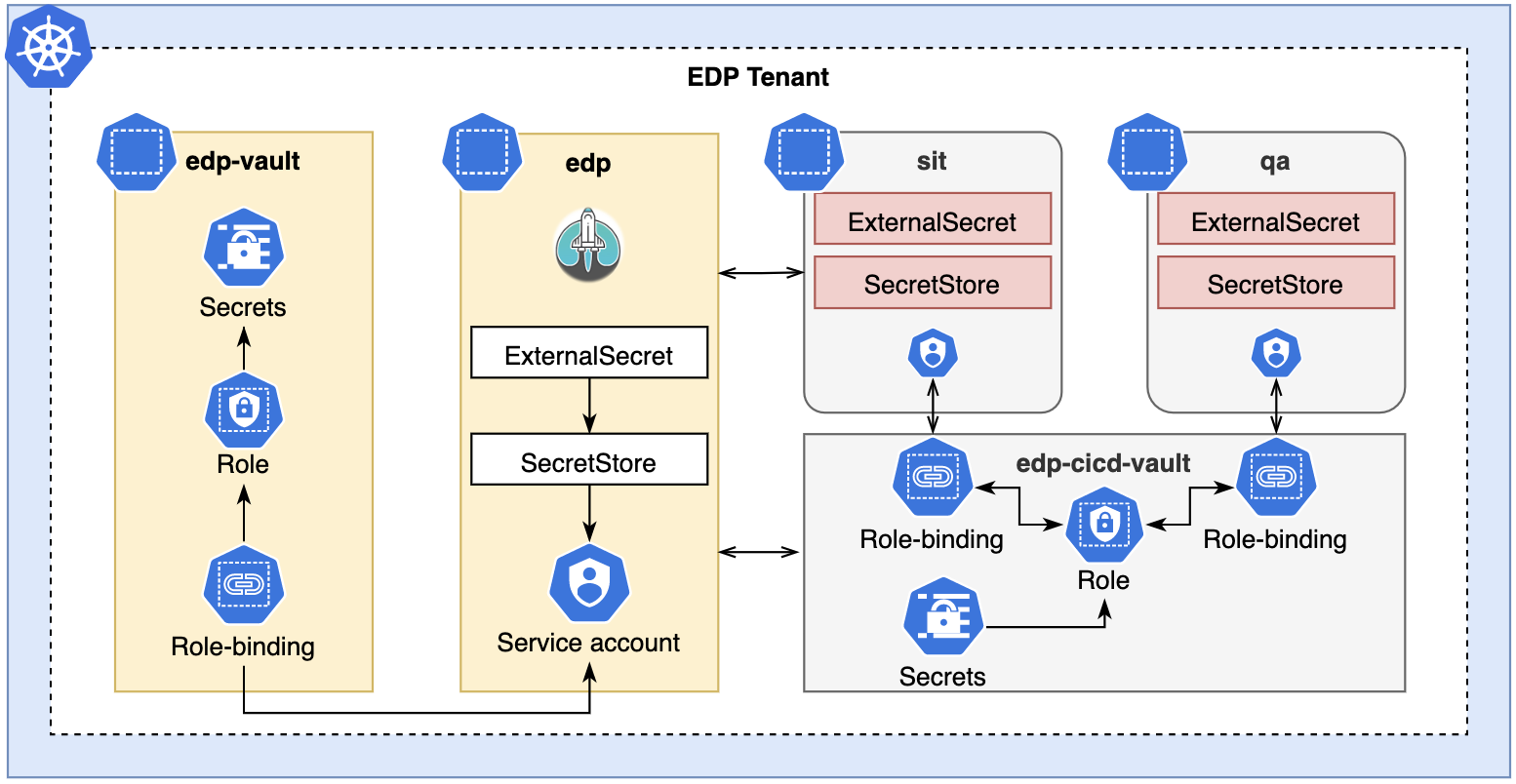
In order to install EDP, a list of passwords must be created. Secrets are provided automatically when using ESO.
-
Create a common namespace for secrets and EDP:
-
Create secrets in the
edp-vaultnamespace: -
In the
edp-vaultnamespace, create a Role with a permission to read secrets: -
In the
edp-vaultnamespace, create a ServiceAccount used bySecretStore: -
Connect the Role from the
edp-vaultnamespace with the ServiceAccount in theedpnamespace: -
Create a SecretStore in the
edpnamespace, and use ServiceAccount for authentication: -
Each secret must be defined by the
ExternalSecretobject. A code example below creates thekeycloaksecret in theedpnamespace based on a secret with the same name in theedp-vaultnamespace:apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata: name: keycloak namespace: edp spec: refreshInterval: 1h secretStoreRef: kind: SecretStore name: edp-vault # target: # name: secret-to-be-created # name of the k8s Secret to be created. metadata.name used if not defined data: - secretKey: username # key to be created remoteRef: key: keycloak # remote secret name property: username # value will be fetched from this field - secretKey: password # key to be created remoteRef: key: keycloak # remote secret name property: password # value will be fetched from this field
Apply the same approach for enabling secrets management in the namespaces used for microservices development, such as sit and qa on the diagram above.
AWS Systems Manager Parameter Store⚓︎
AWS SSM Parameter Store can be used as a Secret Provider for ESO. For EDP, it is recommended to use the IAM Roles For Service Accounts approach (see a diagram below).
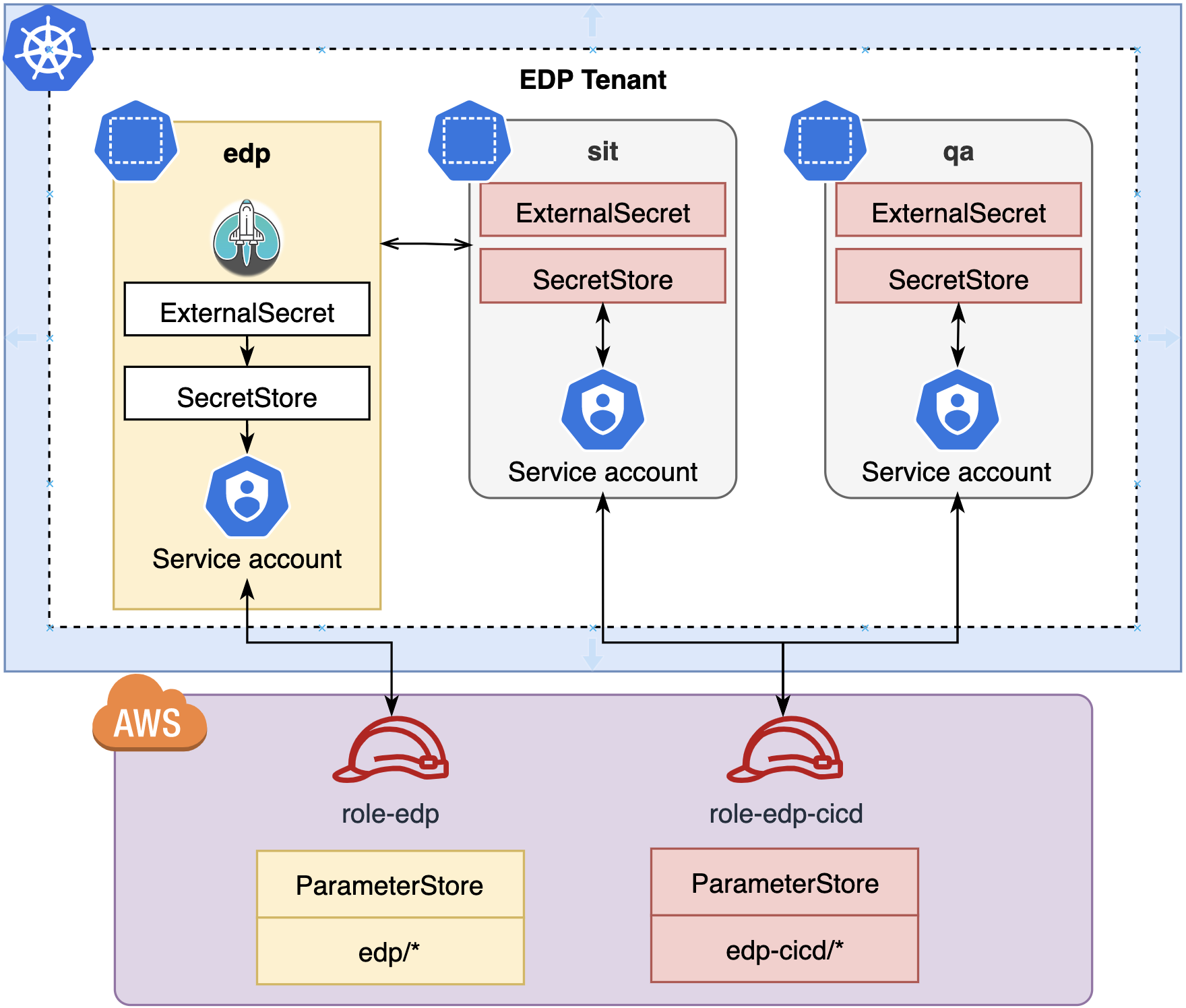
AWS Parameter Store in EDP Scenario⚓︎
In order to install EDP, a list of passwords must be created. Follow the steps below, to get secrets from the SSM:
-
In the AWS, create an AWS IAM policy and an IAM role used by
ServiceAccountinSecretStore. The IAM role must have permissions to get values from the SSM Parameter Store.a. Create an IAM policy that allows to get values from the Parameter Store with the
edp/path. Use yourAWS RegionandAWS Account Id:{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "ssm:GetParameter*", "Resource": "arn:aws:ssm:eu-central-1:012345678910:parameter/edp/*" } ] }b. Create an AWS IAM role with trust relationships (defined below) and attach the IAM policy. Put your string for
Federatedvalue (see more on IRSA enablement for EKS Cluster) and AWS region.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::012345678910:oidc-provider/oidc.eks.eu-central-1.amazonaws.com/id/XXXXXXXXXXXXXXXXXX" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringLike": { "oidc.eks.eu-central-1.amazonaws.com/id/XXXXXXXXXXXXXXXXXX:sub": "system:serviceaccount:edp:*" } } } ] } -
Create a secret in the AWS Parameter Store with the name
/edp/my-json-secret. This secret is represented as a parameter of type string within the AWS Parameter Store:View: Parameter Store JSON
{ "keycloak": { "username": "keycloak-username", "password": "keycloak-password" }, "ci-defectdojo": { "token": "XXXXXXXXXXXX", "url": "https://defectdojo.example.com" }, "kaniko-docker-config": { "auths" : { "registry.com": { "username":"registry-username", "password":"registry-password", "auth": "<base64 encoded 'user:secret' string>" } }}, "regcred": { "auths": { "registry.com": { "username":"registry-username", "password":"registry-password", "auth":"<base64 encoded 'user:secret' string>" } }}, "ci-github": { "id_rsa": "id-rsa-key", "token": "github-token", "secretString": "XXXXXXXXXXXX" }, "ci-gitlab": { "id_rsa": "id-rsa-key", "token": "gitlab-token", "secretString": "XXXXXXXXXXXX" }, "ci-jira": { "username": "jira-username", "password": "jira-password" }, "ci-sonarqube": { "username": "<ci-user>", "secret": "<secret>" }, "ci-nexus": { "username": "<ci.user>", "password": "<secret>" }, "oauth2-proxy-cookie-secret": { "cookie-secret": "XXXXXXXXXXXX" }, "keycloak-client-headlamp-secret": "XXXXXXXXXXXX", "ci-argocd": { "token": "argocd-token", "url": "https://argocd.example.com" }, "ci-dependency-track": { "token": "dependency-track-token", "url": "https://dependency-track.example.com" } } -
Set External Secret operator enabled by updating the values.yaml file:
-
Install/upgrade edp-install: